A new ransomware variant targeting VMware ESXi has been wreaking havoc on organizations worldwide since early February. Dubbed ESXiArgs, the ransomware has breached and encrypted thousands of servers as of February 10. Attackers are exploiting unpatched instances of the two-year-old ESXi OpenSLP Heap Overflow Vulnerability CVE-2021-21974 to gain access and deploy ESXiArgs.
What is ESXiArgs Ransomware?
ESXiArgs is a new Linux-based ransomware targeting VMware ESXi, an enterprise-class, type-1 hypervisor developed by VMware for deploying and serving virtual machines. Details about EXSiArgs were first disclosed by the French National Government Computer Security Incident Response Team (CERT-FR) in an advisory on February 2, 2023. The advisory observes that the ESXiArgs campaign exploits a two-year-old heap overflow vulnerability (CVE-2021-21974) in ESXi’s OpenSLP service. According to the original VMware security advisory dated February 23, 2021, “A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service resulting in remote code execution.” Successful infiltration allows the attacker to load their malicious files onto the server, which would result in the encryption of virtual machines and their data.
CVE-2021-21974 is a patched vulnerability, and attackers are exploiting unpatched instances of ESXi to deploy the ESXiArgs ransomware. CVE-2021-21974 affects the following VMware ESXi versions:
7.x before ESXi70U1c-17325551
6.7.x before ESXi670-202102401-SG
6.5.x before ESXi650-202102101-SG
Summary of CVE-2021-21974
|
Vulnerability Name
|
VMware ESXi OpenSLP Heap Overflow Vulnerability (CVE-2021-21974)
|
|
Disclosed Date
|
23 February 2021
|
|
Vulnerable Component
|
OpenSLP (Service Location Protocol) Service
|
|
Vulnerability Type
|
Heap Overflow Vulnerability
|
|
Affected Versions
|
7.x prior to ESXi70U1c-17325551
6.7.x prior to ESXi670-202102401-SG
6.5.x prior to ESXi650-202102101-SG
|
|
Severity
|
CVSS v3 Base Score: 8.8 (High)
|
|
Exploitability
|
Attack Vector: Adjacent
Attack Complexity: Low
Privileges Required: None
User Interaction: None
|
|
Scope
|
Unchanged
|
|
Impact
|
Confidentiality Impact: High
Integrity Impact: High
Availability Impact: High
|
|
Patch Status
|
Patched
|
The Current State of ESXiArgs Ransomware Attacks
According to a BleepingComputer article updated on February 5, approximately 120 ESXi servers had been encrypted by the end of the first day of attacks. The article also notes that, based on data from Censys Search, the number of compromised ESXi servers reached 2,400 worldwide after a wave of attacks over the weekend, with the majority in Europe. According to a joint Cybersecurity Advisory dated February 8 by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the FBI, the ESXiArgs ransomware campaign has compromised over 3,800 servers globally.
Despite a large number of affected systems, the ESXiArgs campaign has not been particularly successful from the attackers' perspective. In an update to their article on February 6, BleepingComputer reveals that the ransomware payment tracking service Ransomwhere had only tracked four ransom payments for a total of $88,000 up till then.
The low ransom payment figures are most likely attributed to the release of recovery scripts, provided by CISA and by security researcher Enes Sonmez, to help victims rebuild encrypted virtual machines. More information on remediation is provided below.
Technical Details of ESXiArgs Ransomware
Malicious Files
There are five malicious files involved in an ESXiArgs ransomware attack. These files are stored in the server’s /tmp/ folder after it has been compromised. The names and descriptions of the malicious files are shown in the table below.
|
File Name
|
Description
|
|
encrypt
|
The encryptor ELF executable
|
|
encrypt.sh
|
A shell script that acts as the logic for the attack. It performs various tasks before and after executing the encryptor.
|
|
public.pem
|
A public RSA key used to encrypt the key that encrypts a file
|
|
motd
|
The ransom note in text format
|
|
index.html
|
The ransom note in HTML format
|
encrypt.sh
The encrypt.sh shell script performs the following tasks before and after executing the encryptor:
- Modifies an ESXi virtual machine's configuration files (.vmx). The file extensions '.vmdk' (virtual machine disk files) and '.vswp' (virtual machine swap file) are changed to '1.vmdk' and '1.vswp'.
- Terminates all running virtual machines by force-terminating (kill -9) all processes that contain the extension '.vmx'.
- Enumerate all storage volumes on the ESXi host so that virtual disks not attached to the VM may also be encrypted.
The shell script searches storage volumes for files with the following extensions:
- .vmdk
- .vmx
- .vmxf
- .vmsd
- .vmsn
- .vswp
- .vmss
- .nvram
- .vmem
- For each identified file, the script will create a [file_name].args file in the same folder and checks the size of the file.
- Executes the 'encrypt' encryptor to encrypt files based on the computed parameters. For files smaller than 128 MB, the entire file is encrypted in 1MB increments. For files larger than 128 MB, the encryptor alternates between encrypting 1 MB of data and not encrypting chunks (size_step) of data in what is known as intermittent encryption.
- After encryption, the script replaces the ESXi server’s index.html file and motd file with the ransom notes of the same name.
- Deletes various files, including logs, backup files, scheduled tasks, the Python backdoor installed in /store/packages/vmtools.py, all existing IP addresses in the HTTP port configuration file, and the malicious files initially uploaded to the /tmp/ folder.
- Finally, the script executes the /sbin/auto-backup.sh to update the configuration saved in the /bootbank/state.tgz file and starts SSH.
Ransom Note
The name of the ransom note file is "How to Restore Your Files.html". The note claims that "All files have been stolen and encrypted by us." Victims are then asked to pay a ransom in bitcoin to a specified bitcoin address. Upon payment, victims can obtain the decryption key on TOX. Victim organizations are warned that non-payment within three days will result in some exposure of their data, a higher ransom demand, and a threat to notify their customers.
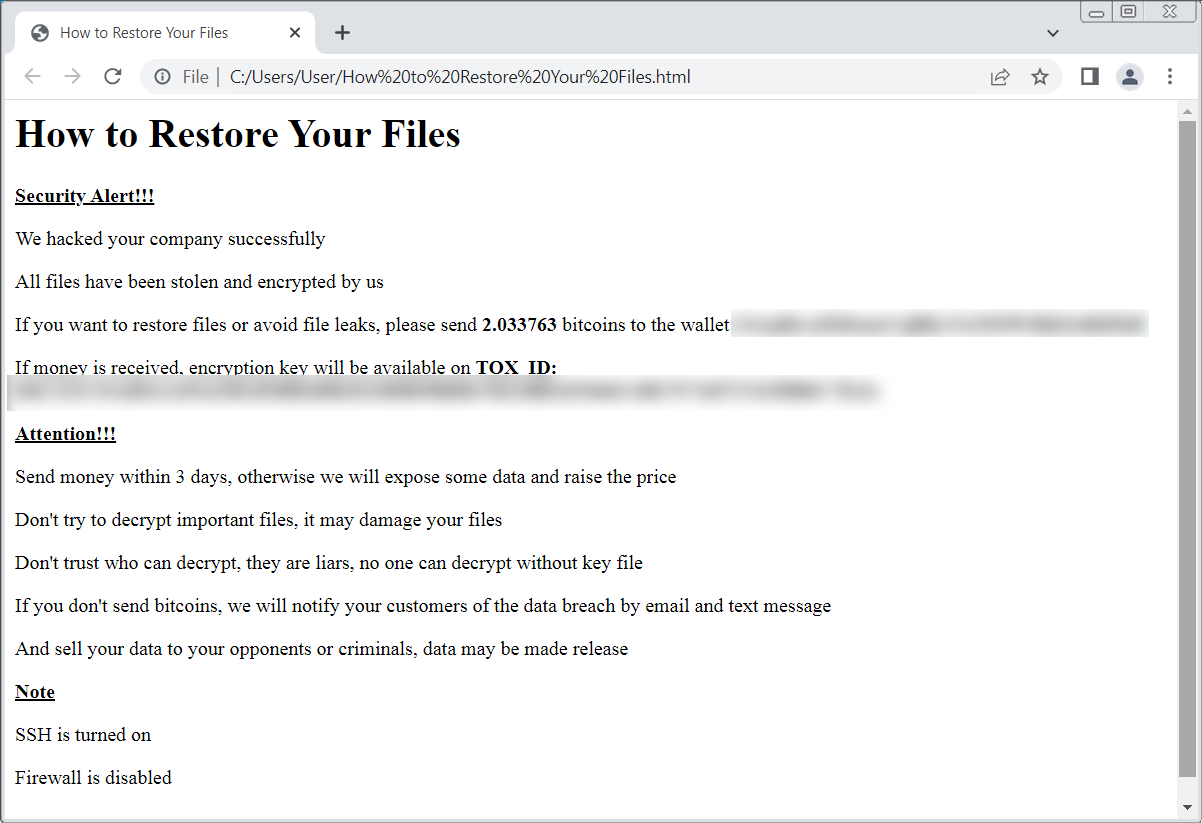
Early ESXiArgs ransom note in later attacks (Source: BleepingComputer)
In an update to their article on February 6, BleepingComputer revealed a slightly revised ESXiArgs ransom note in which a bitcoin address was not provided. Instead, victims are asked to contact the attackers on TOX to obtain the bitcoin address. Removing the bitcoin address was likely done to prevent any payments from getting tracked.
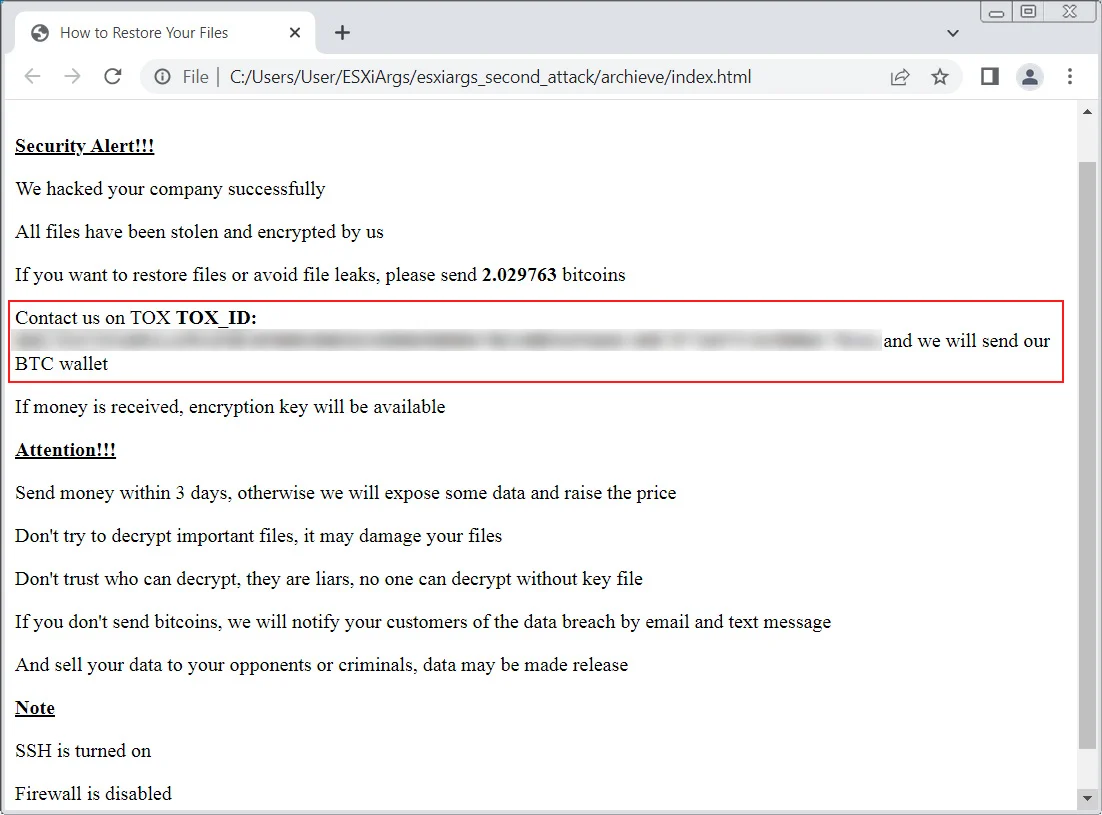
Modified ESXiArgs ransom note in later attacks (Source: BleepingComputer)
Remediation for ESXiArgs Ransomware
-
Update VMware ESXi
On February 6, the VMware Security Response Center published an article advising users to upgrade to the latest version of ESXi, in which OpenSLP has been disabled by default since 2021.
-
Disable OpenSLP
The VMware article above also mentions that users may disable the OpenSLP service to prevent compromise.
However, there are reports of instances where ESXi servers have been breached and encrypted even with OpenSLP disabled.
-
Check For and Remove Malicious Files
ESXi users may check the folders known for storing the malicious files used in an attack, including the /tmp/ folder and the Python backdoor located in /store/packages/vmtools.py. Users are advised to remove these files immediately should they be discovered.
-
Recovery Script
On February 8, CISA released a Cybersecurity Advisory to provide a recovery script for victims of ESXiArgs ransomware attacks to restore their data, with guidance on how to use the script.
Get Protected Against Ransomware with ForeNova
ForeNova offers a diverse range of enterprise cybersecurity products and services to help organizations prevent, detect, and respond to ransomware and all forms of cyber-attacks.


.svg)

.svg)
.svg)







