What is the biggest vulnerability of an enterprise that a cyber-attacker can exploit? Network vulnerabilities? Poorly configured devices? Application vulnerabilities? All valid guesses, but the right answer is: human users.
No matter how foolproof the network or the device security is, an enterprise remains safe from cyberattacks as long as its employees don’t succumb to the guiles of a threat actor. Luring a user into a trap using inducements or threats is called phishing. According to Verizon’s Data Breach Investigations Report 2021, 22% of all data breaches in enterprises involved phishing attacks; 85% of these incidents involved the human element. What should ring the alarm bells is the fact that 75% of the organizations around the world were victims of phishing attacks in 2020.
Phishing attacks have seen an uptick due to the remote job culture in the aftermath of the COVID-19 pandemic. Communication between employees has shifted to online platforms like email and other chat services. Most enterprises now have employees who have not even seen each other! Increased online activity and unfamiliarity between employees have made the jobs easier for attackers.
Phishing is the most common type of cyberattack that uses social engineering tricks. The attackers send well-crafted messages to their targets to manipulate their behavior and induce a response that eventually compromises the security of the device or network. The response includes making the target click a link embedded in the message or fooling them into downloading a malicious file. While the link usually redirects the user to a malicious website, the downloaded file installs malware into the target system, thereby opening the floodgates for the attacker.
The phishing messages are crafted to look legitimate and believable. The underlining message invariably induces a sense of urgency or panic in the target’s mind. For example, some users get an email – seemingly from one of the online services they use – saying their account has been restricted and they will need to download the attached file, update their login information to continue using the services.

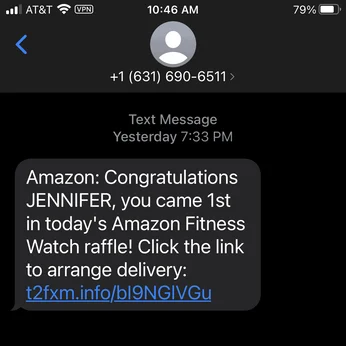
Another type of phishing message taps into human greed, where the message implies that the target has won a voucher or a gift. It also instructs targets to click the link to claim the gift before it expires. Some users download the attached file, and nothing good comes from it. Once victims download and open this file, threat actors get unauthorized access to their system.
Based on how the messages are delivered or whom it targets, there are several types of phishing attacks. We’ll discuss some of the most common ones here.
The source of the phishing message is an email that links to malicious sites or includes malicious attachments. The attachments are often in HTML or Docx format and contain executable codes.
It’s a lot like phishing, but it’s more organized and targets a particular individual or organization. The attacker usually does a lot of groundwork before laying the trap. Usually, the threat actor assumes the identity of a senior-level executive and targets the lower-level employees, requesting sensitive data or login credentials from the latter.
Whaling attacks target a particular individual who is regarded as high-value personnel at an enterprise, like C-suites. The target is called a ‘whale’ owing to the figurative size of the individual in the company. Whaling is highly rewarding for attackers as senior executives have high-level access to data.
In whaling, the threat actor assumes the identity of another senior executive and starts a legitimate conversation over a few weeks via email or an office chatting platform. Once the attacker gains the whale’s trust, they casually ask for sensitive information like login credentials. Completely ensnared, the whale often ends up divulging details.
SSL certificates are to protect important data of a site’s visitors; the HTTPS prefix on a website’s URL builds trust with users. But some attackers lure unsuspecting users by flaunting fraudulent HTTPS sites and harvesting their data.
It’s standard phishing, but via phone call. Usually, the attackers call the targets on the phone pretending to be the customer service executive. They can be very convincing and make you spill out sensitive information on short notice. Just like email phishing, the attackers create a sense of urgency so that you don’t get much time to double-check.
Phishing messages sent on the target’s phone as SMS is called smishing. It mostly contains a link to a malicious website. The short message will trigger panic and force the user to commit mistakes.
4.48 billion people across the globe use social media; it’s no surprise then that threat actors use the medium for phishing attacks. It works a lot like email or SMS phishing except the attacker texts the target on social media. Usually, attackers pretend to be customer service agents, reaching out to users to resolve their grievances.
A Clone phishing attack involves the attacker copying and resending an old message to the victim. This old message might have been part of a conversation between the target and a third party. The attacker first pretends to be the third party, using a seemingly legitimate mail id or phone number, and sends this message again, saying something like “resending this for your reference”. But this time, the links in the original message will be replaced by malicious links.
Popups are used by legitimate websites to deliver important information to their visitors and also for marketing purposes. But when users pass by infected websites, they are met with pop-ups about a problem with the device security like an antivirus or firewall issue. At least some users fall for it and click on these pop-ups, which are essentially the gateway to malware attacks.
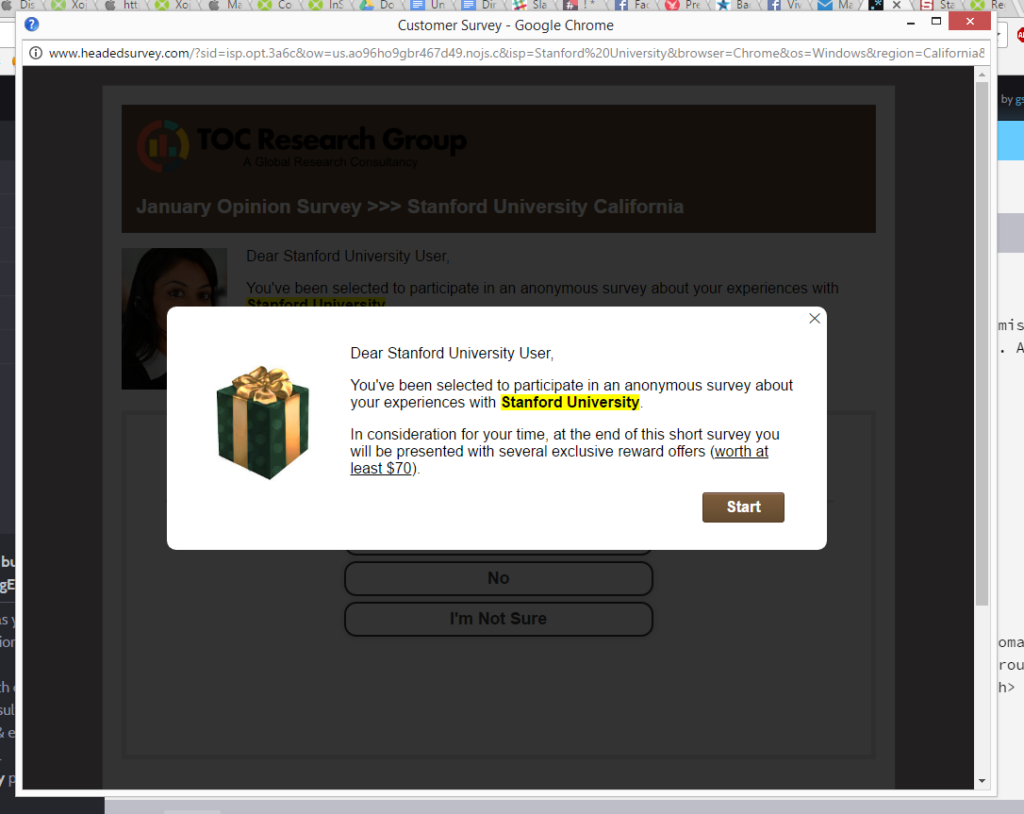
The reason why threat actors often find success in phishing is that they exploit the greatest vulnerability of all: human emotions. A phishing attack becomes successful only if the user falls for social engineering tricks. So, the trick is to be careful. Good awareness and experience can help you detect almost all types of phishing attacks. Here’s how:
A blueprint for combatting ransomware in the manufacturing industry
Insider threats are becoming center stage to some of the deadliest cyberattacks in recent news.

Novacommand can help detect threats by inspecting and analyzing the network traffic. The information about the network traffic (metadata) will be correlated and analyzed as well.
By doing this, threats can be detected in an early stage by their behavior, destination, or a combination of both.
Novacommand will not ‘defend’ you against threats but will alarm you on a threat and if needed initiate an action with a 3rd party integration like a firewall or EPP.
While standard phishing attacks target anyone at a firm with templated messages, spear phishing targets specific individuals in the firm; the attacker often does a good amount of research on the target. Spear phishing emails are carefully crafted and extremely personalized, making them difficult to detect.
Please wait while you are redirected to the right page...
When you visit our website, ForeNova and third parties can place cookies on your computer. These cookies are used to improve your website experience and provide more personalized services to you, both on this website and through other media. To find out more about the cookies we use, see our Privacy Policy.
If you reject all cookies, except one strictly necessary cookie, we won't track your information when you visit our site. In order to comply with your preferences, we'll have to use just one tiny cookie so that you're not asked to make this choice again.