Cyber threats exist and continue to evolve, period. Left unchecked and unprepared, the havoc threats can wreak extends beyond an organization’s IT, network, and cloud infrastructures, causing business disruption, data and monetary losses, and damage to reputation, to name a few. There are plenty of grim stories of companies—especially the small and mid-sized players—succumbing to cyber threats and attacks. This is where threat detection and response (TDR) places companies in a better position to identify threats and proactively minimize/avoid their damaging impact.
Threat detection is the practice of holistically analyzing the entirety of an organization’s security stance and IT ecosystem to identify any malicious activity or vulnerability that could compromise the network. Mitigation efforts ought to be enacted upon detecting threats to neutralize them properly.
To begin with, it is very important to understand the types of prevalent cyber security threats.
Several types of cyber threats pose varying degrees of danger to an organization’s IT infrastructure. Some of the most common and damaging ones include:
• Malware
Malware infects systems via malicious links or e-mail, though it can be delivered in several other ways. They are designed to block access to critical network components, damage systems, and collect sensitive data. Malware can be categorized as follows:
– Spyware: Enables black hats to obtain information within and about the targeted systems. Spyware does not act immediately to avoid detection but gathers data over time. And it’s often too late by the time it is detected. Keylogging software is a good example of spyware.
– Ransomware: They block access to a system via encryption and demand payment (ransom) in exchange for the decryption key. They are relatively new threats and have become notoriously common, often bankrupting organizations. Plenty of public establishments such as government offices, hospitals, and even courts have become victims of ransomware attacks. WannaCry is an excellent example of a ransomware attack that affected organizations and systems worldwide.
– Trojan Horses: They are essentially codes that pretend to be legitimate within a device but load in malware or virus. Undetected, they work in the background reading passwords, recording keyboard strokes, and deleting, blocking, modifying, or copying data. The Pegasus software from the Israeli manufacturer NSO is an infamous example of a Trojan.
– Scareware: A scareware floods a system with false warnings about viruses and threats that don’t exist. It tricks them into downloading “protection” software that loads malware into the system.
• Phishing
Put simply, phishing is a manipulative attempt to misguide users into thinking that they are interacting with a legit organization, be it via e-mail, phone calls, or even fake websites that appear valid and genuine. It is even more difficult to evade spear phishing, a more targeted version of phishing, with messages tailored to the individual. Phishing falls under the category of social engineering, a type of cyber manipulation that exploits human vulnerabilities/sentiments to gain private information, access networks, or avail unauthorized services. It involves manipulating unsuspecting users or employees into making decisions, revealing data for malicious reasons, spreading malware infections, or giving away access to restricted systems. Baiting is another form of social engineering that involves luring victims (unsuspecting users) with highly attractive offers, playing mind games on their greed or temptation, causing them to ‘activate’ cyber threats.
• DDoS
A distributed denial-of-service (DDoS) attack is a malicious attempt to overwhelm a targeted server, service, or network with fake traffic—bots and botnets (collection of bots)— to cause disruption. Upon establishing and botnet, the attacker can direct an attack by delivering remote instructions to each bot.
• Blended Threat
A blended threat employs a variety of techniques and attack vectors, such as programs that mix the functionalities of Trojans, worms, and backdoors to attack a system simultaneously. The most prevalent blended threat distributes links to websites where malware or spyware is stealthily downloaded to computers via spam e-mail messages, instant messages, or legitimate websites.
• Zero-Day Threat
A zero-day threat, also known as a zero-hour threat, takes advantage of a potentially serious software security vulnerability that the vendor or developer is unaware of. It hasn’t been discovered before and doesn’t match any known malware signatures. Since zero-days remain unknown and undiscovered, the developer may not have developed a patch for it yet.
• Advanced Persistent Threat (APT)
An APT is a sophisticated cyber-attack that comprises long-term surveillance and intelligence gathering attempts to steal sensitive information or target systems. APTs work best when the attacker remains undetected. The threat actor is typically a nation-state or a state-sponsored group.
Having a robust detection system is the first step in any TDR effort.
Within the context of an organization’s cybersecurity, the notion of threat detection is complex. Being prepared with robust security programs for a worst-case scenario is not too much of an asking in this context because a malicious actor can bypass even the most advanced defensive and predictive technologies. Therefore, a comprehensive threat detection process is integral to a successful TDR effort.
Listed below, are the steps it takes to detect a cyber threat accurately:
Asset discovery involves keeping track of the active and inactive assets on a network. For many corporations, assets include cloud, virtual, and mobile devices in addition to the traditional on-premise workstations and servers. Asset discovery is among the foundational practices that organizations should consider when coming up with a plan to manage their underlying assets and create a more secure IT ecosystem.
Vulnerability scanning entails identifying security weaknesses and flaws in computer networks (including cloud) and software. It identifies weaknesses in a system before they can be exploited. However, running a vulnerability scan has its own set of risks because it is inherently intrusive on the running code on the target system. As a result, the scan can cause errors and reboots, reducing productivity, at least temporarily. Nonetheless, the benefits of vulnerability scanning far outweigh this potential drawback and ultimately enforce an organizations’ security stance.
Network traffic analysis (NTA) is a method of monitoring network availability and activity to identify anomalies, including security and operational issues. This gives organizations the insights needed to optimize network performance, minimize the attack surface, improve security posture, and manage resources effectively. NTA generally includes:
Threat isolation pertains more to e-mail and browser isolation to protect users and endpoints from malware. By isolating suspicious links and downloads remotely, users will avoid falling prey to spear phishing, ransomware, and other sophisticated attacks. Traditionally, organizations have relied on many security solutions for web-based malware protection. Some solutions include using an algorithm to determine if the web content coming into a network is good or bad. Other solutions block users from navigating to websites that might contain harmful code. Examples of these security products include web proxies and secure web gateways.
Deception Technology is a cybersecurity defense practice that baits infiltrators into strategically placed decoys throughout the network. When an attacker trips over one of these traps, a signal is triggered, generating reports and recording the intruder’s actions, providing reliable forensics to see what attackers are doing and where they are going within the network. The gathered information allows security personnel to see what parts of the network the attackers are targeting and form a predictive defense.
Threat hunting entails using manual or machine-based techniques to identify security incidents or threats that have slipped through automated detection methods. To succeed with threat hunting, analysts need to know how to manipulate their tools to find the most dangerous threats.
They also require extensive knowledge about different types of malware, exploits, and network protocols and should be adept at navigating through large volumes of data. A threat hunt allows security analysts to actively go out into their network, endpoints, and security equipment to look for threats or attackers, hitherto unnoticed, rather than waiting for a threat to manifest. Threat detection technologies for security events, networks, and endpoints can help organizations avoid prevalent cybersecurity adversaries.
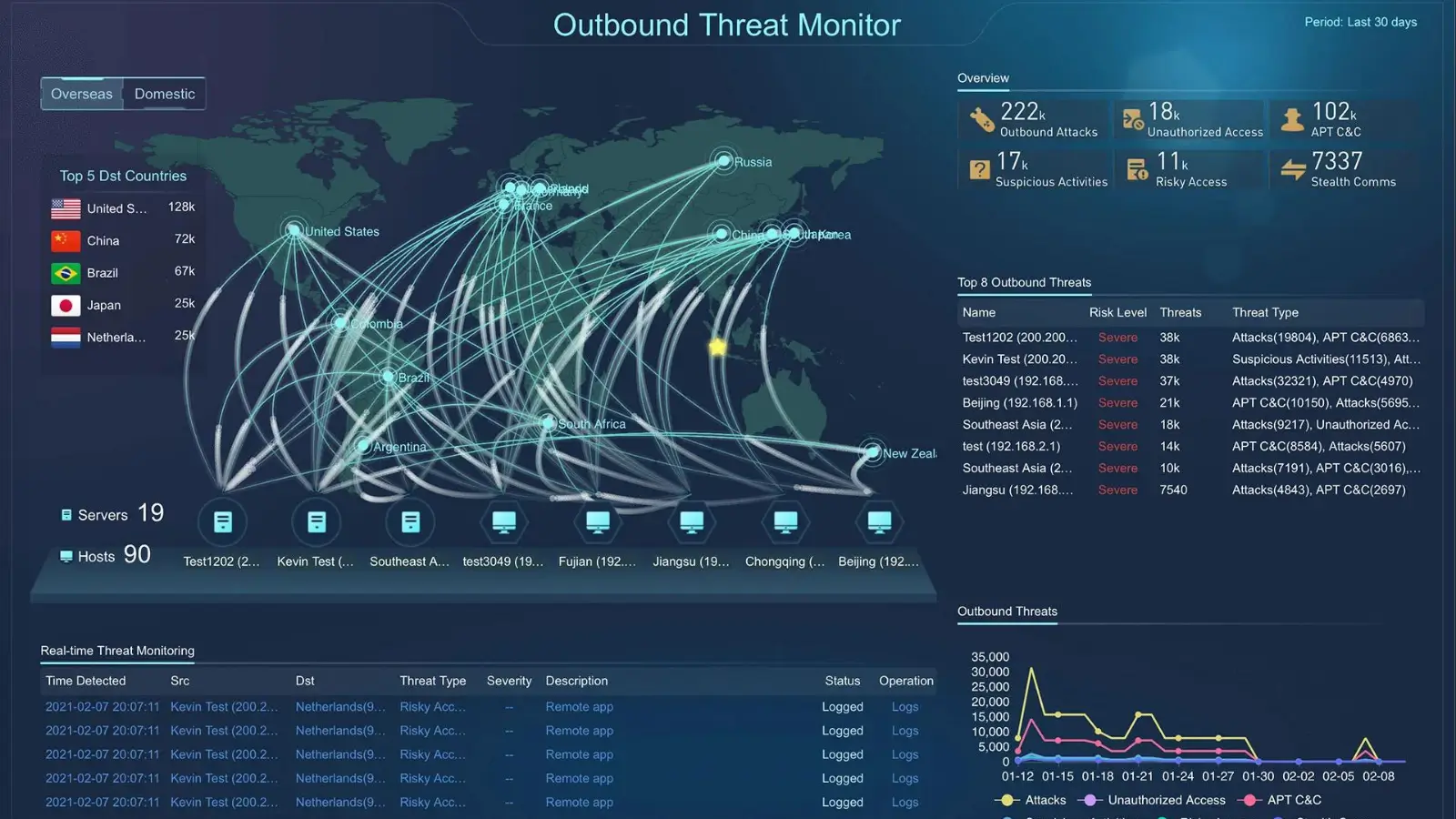
Threat detection and threat analysis/analytics allow organizations to understand their IT vulnerabilities better and proactively improve their security stance via the right threat response. Enterprises can avert potential attacks and incidents and better forecast their impact. It enables cybersecurity teams to identify known, unknown (like a zero-day threat), and emerging threats early on, allowing them to safeguard and defend their systems.
The ultimate goal of threat detection is to investigate potential compromises and improve cyber defenses. Apart from preventing attacks, TDR enables protecting business data, avoiding costly downtime, complying with cybersecurity mandates and other regulations, and, more importantly, peace of mind for the users and leaders.
The dangers of cyber threats are numerous and widespread. Regular assessments, system evaluations, and following well-aligned TDR actions are required to identify vulnerabilities that could be exploited and reduce the likelihood of an organization falling victim to an incident or cyber attack. Security is a constantly evolving cat-and-mouse game between the good and the bad players, with no absolute unit solution to ensure complete protection. There are myriad tools, processes, and strategies that can help businesses be as safe as possible. Organizations can only rely on the best practices and implement tried and tested solutions to strengthen their ability to identify attacks as soon as they occur.

Novacommand can help detect threats by inspecting and analyzing the network traffic. The information about the network traffic (metadata) will be correlated and analyzed as well.
By doing this, threats can be detected in an early stage by their behavior, destination, or a combination of both.
Novacommand will not ‘defend’ you against threats but will alarm you on a threat and if needed initiate an action with a 3rd party integration like a firewall or EPP.
A blueprint for combatting ransomware in the manufacturing industry
Insider threats are becoming center stage to some of the deadliest cyberattacks in recent news.
We identify threats based on two major methods:
IDS is more focused on north-south traffic only (perimeter traffic) and uses old-school CTI only to detect threats.
So, if the ‘threat’ is not in the database, an IDS will not give you an alert.
Depends on how you look at the firewall. ‘next-gen’ firewalls have IDS capabilities built in, while older firewalls work with static rules to inspect traffic and block it if it hits a specific ruleset.
IPS is IDS but then also protective. It might block the malware on the host (HIDS/HIPS) or on the network (NIDS/ NIPS), where IDS is a detecting tool.
IDS can detect malware, but most of the time ‘known’ malware as the signature needs to be in the database of the IDS solution.
This is a tricky question.
From a company perspective, Firewall to protect the (perimeter) network (also micro-segmentation), Endpoint protection to secure the servers and workplaces. And as a third pilar NDR to detect and respond to threats in the lateral environment. (internal traffic not traveling through the firewall or EPP solution)
Please wait while you are redirected to the right page...
When you visit our website, ForeNova and third parties can place cookies on your computer. These cookies are used to improve your website experience and provide more personalized services to you, both on this website and through other media. To find out more about the cookies we use, see our Privacy Policy.
If you reject all cookies, except one strictly necessary cookie, we won't track your information when you visit our site. In order to comply with your preferences, we'll have to use just one tiny cookie so that you're not asked to make this choice again.