Cyber threats present a real danger as the world moves towards a near-total digital age, although the digital era began in the 1980s.

With a higher dependency on digital devices and the Internet during the pandemic, cyber threats have only gone up.
The findings of a new report from McAfee Enterprise and FireEye indicate that during the pandemic, 81% of global organizations experienced increased cyber threats, with 79% experiencing downtime due to a cyber incident during a peak season.
Businesses and government organizations are hit by cyber attacks, often unexpectedly. Attacks come in the form of denial of service (DoS) attacks, viruses, malware, spyware, or merely because of a phishing email link that an employee unintentionally clicked. When ignored or not prevented, cyber threats result in service or business discontinuity, data loss, system or application unavailability, blackouts, military equipment or government system failure, and network disruption.
A cyber security threat refers to the danger of a malicious attempt to steal data and cause damage or disruption to computer systems, networks or assets by gaining unauthorized access or invading through other means. Businesses perform a cyber threat analysis to identify, remediate, and prepare for potential threats.


Cyber threat analysis is a necessary safety procedure that blends vulnerability analysis with a risk assessment. It provides a deeper understanding of the potential risks to a particular network by relating information about vulnerabilities in an organization’s network to real-world cyber threats. It is a structured and repeatable process.
Cyber threat analysis helps identify, prepare, and prevent attacks by providing information on attackers, their motives, and capabilities. Threat analysis and intelligence prepare organizations to formulate proactive analytics and mitigation strategies, instead of merely reacting to individual cyber attacks. Threat intelligence helps organizations with valuable knowledge about these threats, build effective defense mechanisms, and mitigate the risks that could cause financial and reputational damage. It is challenging to combat cyber-attacks effectively without understanding security vulnerabilities, threat indicators, and how threats are carried out.
A proper risk assessment of the threats is a must for organizations of all sizes and industry types to avoid being caught unaware when an actual security incident occurs. A cyber security risk assessment is the process of identifying, analyzing, and evaluating risk.
Threat hunts begin with identifying all endpoints and network assets. Creating a network architecture diagram from the asset inventory list is a great way to visualize the interconnectivity and communication paths between assets, processes, and entry points into the network.
Since most malware communicates with external entities through the network, hunters will often scour that network for artifacts containing malicious content. Hunters will pay attention to the listening ports utilizing TCP/UDP ports such as SMTP, HTTP, FTP, and proxy servers. Also, set up external monitoring servers to aid in traffic monitoring.
A trigger is a step in the threat-hunting framework that guides threat hunters to a specific system or area of the network for further investigation. Here, advanced detection tools identify unusual actions that may be indicators of malicious activity. Often, a hypothesis about a new threat can be the trigger for proactive hunting. A hypothesis describes threats that might be in the environment and the optimal methods of detecting them. It’s best to combine indicators of compromise, environmental factors, and industry experience to create the most effective threat hunts.
During the investigation phase, the threat analyst uses various technologies, such as Endpoint Detection and Response (EDR), to conduct a deep dive into a potential attack or compromised system. The investigation continues until the search is deemed unnecessary or a thorough picture of the malicious behavior emerges.
Automated systems help in detecting and mitigating threats. These actions can include removing malware files, restoring altered or deleted files to their original state, updating firewall /IPS rules, deploying security patches, and changing system configurations. During the resolution phase, the information collected during the investigation phase is relayed to other teams and tools that can respond, prioritize, analyze, or store the information for future use. The gathered information is used to predict trends, prioritize, and remediate vulnerabilities, and improve security measures.
Throughout this process, cyber threat hunters gather as much information as possible about an attacker’s actions, methods, and goals. They also analyze collected data to determine trends in an organization’s security environment, eliminate current vulnerabilities, and make predictions to enhance security in the future.
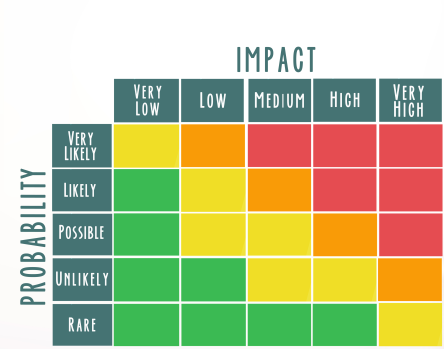
Cyber security risk assessment is an integral part of an organization’s enterprise risk management process. By conducting a risk assessment, organizations will be able to identify potential adverse events that are often a result of malicious acts by threat actors, determine the levels of cyber security risk that they are exposed to, and create a risk-aware culture within the organization.
As an important step in the risk evaluation process, analysts use a 5-by-5-risk matrix to determine the risk level based on the “Likelihood” and “Impact” of a particular risk scenario.
There are situations or areas where there is no point in pursuing a risk that is unlikely to occur or will cause insignificant damage.
Today’s cyber threat scenario demands more vigilance and protection because ongoing attacks on crucial infrastructure can overwhelm even laypersons. It is essential to know the risks and the extent of exposure to such attacks and to have a proactive rather than reactive strategy to thwart cyber attacks.
The main objective of cyber threat analysis is to arrive at answers that can help create and support counter-intelligence investigations, leading to the elimination of threats.
The final output from a threat assessment should provide the best practices using protective controls to endorse integrity, availability, and privacy.
Using cyber intelligence security specialists can stop attacks and contain them faster, saving considerable monetary losses that cyber attacks impose. Threat intelligence can improve cyber security for companies at every level, including network security and cloud security levels. The threat intelligence analysts play a crucial role in planning, analyzing, and enabling organizations to make tactical decisions based on the actionable intelligence gathered through the various methods mentioned in this article.

Stop ransomware before the point of no return with a complete view of your network environment
A blueprint for combatting ransomware in the manufacturing industry
Insider threats are becoming center stage to some of the deadliest cyberattacks in recent news.
While a threat is a possible security breach that can exploit the vulnerability of a system or asset, an attack is a deliberate unauthorized action on a system or asset. Threat modeling is a structured process that helps an organization document known security threats and arrive at rational decisions to address them. It varies from an attack tree, a conceptual diagram showing how that system might be attacked.
Generally, threat detection relies on four major methods: Configuration, Modeling, Indicator, and Threat Behavior. Each category supports different requirements; hence, the type of detection best suited for an organization depends on their business requirement.
The costs involved with data storage and licensing can make analysis more difficult, as can running queries against large amounts of data. The given context and the complexity of the threat also hinder the efficacy of the decisions made to eliminate specific threats.
Please wait while you are redirected to the right page...
When you visit our website, ForeNova and third parties can place cookies on your computer. These cookies are used to improve your website experience and provide more personalized services to you, both on this website and through other media. To find out more about the cookies we use, see our Privacy Policy.
If you reject all cookies, except one strictly necessary cookie, we won't track your information when you visit our site. In order to comply with your preferences, we'll have to use just one tiny cookie so that you're not asked to make this choice again.