Meet the cybersecurity detection compliance requirements to support your automotive compliance certification with NovaMDR – a cost-effective 24/7 managed detection and response service built for SMEs in the German Automotive Industry.

TISAX® (Trusted Information Security Assessment Exchange) is a certification framework specifically designed for the automotive industry. It was developed by the German Association of the Automotive Industry (VDA) to ensure that companies in the automotive supply chain meet high standards of information security.
Automotive compliance is not just a checkbox; it’s a prerequisite for doing business.
Without it, local German automotive suppliers find themselves locked out of lucrative contracts and partnerships, unable to access the vast opportunities that the automotive industry offers.
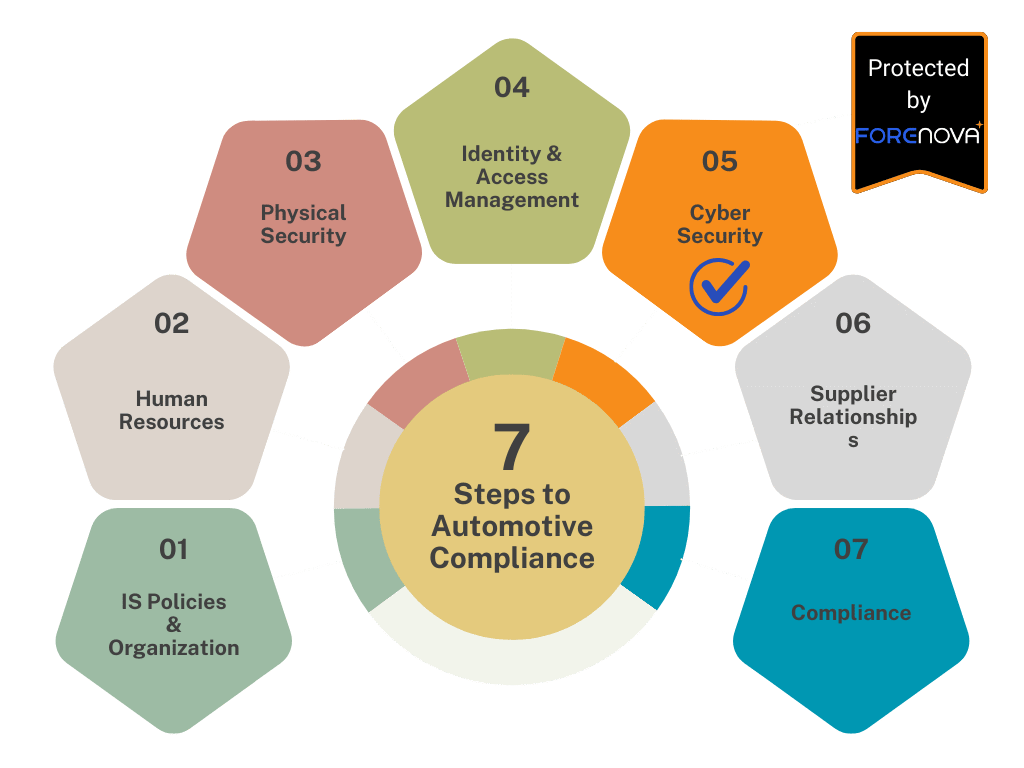
Automotive compliance regulations require companies to reach at least maturity level 3 in each of the seven mandatory categories mentioned above.
Maturity level 3 means that a standard process is consistently followed and integrated into the overall system. The relationships with other processes are documented, and suitable interfaces are created. There is clear evidence that this process has been used reliably and actively over a long time.
Each category has its own specific requirements:
The extent of the information security policies available and if they’re adapted to the organization’s goal is the main concern.
It also includes listing out responsibilities between external IT service providers and own organization, as well as asset management – specifically, how assets are discovered, secured, and assigned.
Information Security Risk Management needs to have a person responsible for the assessment and risk assessments need to be carried out at regular intervals in response to events.
The organization must identify sensitive work areas and define job-specific requirements for employees, ensuring these requirements are met.
It is essential to verify the identities of potential employees by checking their identity documents.
A non-disclosure obligation and adherence to information security policies must be enforced.
Employees should receive training to increase their awareness of security practices.
For teleworking, the organization needs to establish and fulfill requirements that address secure handling of information, appropriate behavior in both private and public settings, and protective measures against theft in public areas.
Access to the organization’s network should be secured through a connection like a VPN, along with strong authentication measures in place.
A security zone concept must be established, incorporating protective measures aligned with the handling of information assets. This concept should consider the physical conditions of premises, buildings, and spaces, including delivery and shipping areas. The defined protective measures need to be implemented, and all individuals involved should be aware of the code of conduct for these security zones.
Requirements for handling supporting assets, such as transport, storage, repair, loss, return, and disposal, must be clearly defined and fulfilled. Additionally, requirements for mobile IT devices and mobile data storage devices should also be established and met, focusing on aspects like encryption, access protection (such as PINs or passwords), and proper marking, especially for situations involving customer interactions.
Requirements for managing identification means throughout their lifecycle must be established, covering creation, handover, return, destruction, validity periods, traceability, and loss handling.
User authentication procedures should be based on a risk assessment that considers potential attack scenarios. State-of-the-art methods must be implemented.
User account management should include creating, changing, and deleting unique and personalized accounts, with collective accounts regulated for traceability. Accounts must be disabled immediately upon employee departure, and regular reviews should be conducted. Login information should be securely provided, with a policy in place to prevent disclosure, unencrypted storage, and ensure quality requirements for authentication information.
Access rights management must include established procedures for application, verification, and approval, following the principle of least privilege. Access rights should be revoked when no longer needed, and regular reviews should be conducted for all user accounts.
All cryptographic procedures used must meet industry standards for security, as legally feasible. Network services for information transfer should be identified, documented, and governed by defined policies that ensure protection against unauthorized access.
Information security requirements for organizational changes, business processes, and IT systems must be determined and applied. IT systems should undergo risk assessments to justify their separation into development, testing, and operational environments, with segmentation implemented accordingly.
Requirements for malware protection must be established, with both technical and organizational measures in place. Information security requirements for event log handling should be identified and fulfilled, ensuring logging of activities by system administrators and users is assessed and monitored, especially when using external IT services.
Technical vulnerabilities in IT systems must be identified, assessed, and addressed based on gathered information. Requirements for auditing IT systems should be determined, with audits coordinated with relevant stakeholders and results reported to management.
Network management and control requirements must be fulfilled, including network segmentation. Critical IT services should be identified, with continuity and recovery responsibilities known to stakeholders. Backup and recovery concepts for relevant IT systems must be established, ensuring data confidentiality, integrity, and availability.
Contractors and cooperation partners must undergo a risk assessment regarding information security, ensuring an appropriate level of security through contractual agreements. Any relevant agreements with clients should be communicated to contractors and cooperation partners, and compliance with these agreements must be verified.
Non-disclosure requirements should be established and fulfilled, with all individuals involved in sharing protected information aware of the requirements and procedures for non-disclosure agreements. Valid agreements must be in place before forwarding sensitive information, and the related requirements and procedures should be reviewed regularly.
Legal, regulatory, and contractual provisions relevant to information security must be regularly identified. Policies for compliance with these provisions should be defined, implemented, and communicated to responsible individuals.
Information security requirements concerning the processing of personally identifiable data must be established, with regulations for compliance known to entrusted personnel. Additionally, processes and procedures for protecting personally identifiable data should be integrated into the information security management system.

Major automotive manufacturers like BMW, Porsche, Mercedes, VW, Ford and others require their suppliers to demonstrate robust information security practices through automotive compliance certification.
Your potential clients view compliance as a non-negotiable standard, and without it, your business risks being overlooked in favor of competitors who have successfully navigated the compliance landscape.

The lack of compliance can severely limit your ability to engage with key players in the market, stifling growth and innovation.
Automotive compliance can feel overwhelming, especially for local German automotive companies that may lack the necessary in-house expertise and resources.
It’s a real struggle to implement the comprehensive security measures required by regulators with limited budgets and personnel.
Companies feel overwhelmed, risking both their compliance status and overall cybersecurity resilience.

You may also lack the necessary expertise to respond effectively to security incidents or breaches, having a skilled team that understands the nuances of threat detection, incident response, and recovery is crucial.
Relying solely on antivirus and firewall solutions is insufficient for compliance and your overall security, therefore you need comprehensive security measures and continuous monitoring to protect sensitive data and systems.
Our customer is one of the leading automotive suppliers globally, providing essential elements of the supply chain to car manufacturers in Europe, the United States, Latin America, and Asia.
Driven by constant innovation, the customer must reliably develop, manufacture, and deliver on time.
Any disruption in manufacturing poses a significant financial risk and threatens the supplier’s impeccable reputation.
“Before we started working with ForeNova, our security team was constantly overwhelmed by the number of threats and incidents they had to deal with. The NovaMDR solution has truly been a game-changer for our organization.”
CTO of the automotive supplier
NovaMDR implemented a tailored Managed Detection and Response service, conducting a thorough assessment of their systems.
We enhanced their security posture with advanced threat detection, continuous monitoring, and incident response strategies aligned with compliance standards.
“Our production efficiency has increased dramatically, and we have more confidence in our ability to protect our systems from future threats”
CTO of the automotive supplier
Automotive Compliance is Essential, don’t risk losing any contracts.
Unlock new business opportunities in the automotive industry while enhancing your cybersecurity defenses.
Gain trust with major automotive manufacturers and maximize your business potential by becoming automotive compliant with NovaMDR.
Business hours don’t count for cyber threats, that’s why our cost-effective Managed Detection and Response service (NovaMDR) gets you 24/7 monitoring and support from a whole team of cybersecurity experts.
With NovaMDR you get advanced threat detection, continuous monitoring, and incident response, providing a robust security framework that protects your sensitive data and systems against evolving cyber threats.
NovaMDR helps local automotive SMEs in Germany efficiently simplify the process of automotive compliance for cybersecurity without breaking the bank by providing a custom and managed solution based on your individual needs.
General Line: +49 8926 200 920
Monday – Friday | 09:00-17:00
ForeNova Technologies GmbH, Sulzbacher Str. 48, 90489 Nürnberg, Germany
TISAX® (Trusted Information Security Assessment Exchange) is a certification standard designed for the automotive industry to ensure the protection of sensitive data. It establishes a framework for assessing information security practices among suppliers and manufacturers.
TISAX® is a registered trademark of the ENX Association and ENX bears no responsibility for the content of the services offered by ForeNova Technologies B.V.
Automotive compliance is crucial for maintaining trust and credibility in the automotive supply chain. It helps organizations demonstrate their commitment to data security, thereby enhancing their reputation and enabling them to win contracts with major automotive manufacturers.
MDR services provide continuous monitoring, threat detection, and incident response to protect organizations from cyber threats. These services help businesses maintain a strong security posture and comply with industry standards.
MDR services streamline the compliance process by implementing advanced security measures, conducting regular assessments, and providing expert guidance. This ensures that your organization meets the cybersecurity requirements for automotive compliance efficiently and effectively.
NovaMDR offers tailored solutions that enhance your cybersecurity defenses, reduce the risk of data breaches, and simplifies the TISAX® compliance process. Our experts help you solve the cybersecurity requirement part of the automotive compliance by providing 24/7 monitoring, threat detection and incident response.
The timeline for achieving compliance varies based on your organization’s current security posture and readiness.
Keep in mind that compliance requires physical security, supplier management, awareness and training, as well as legal and regulatory aspects to be met.
However, with NovaMDR’s support, many clients experience a faster and more streamlined compliance process.
While certification is not legally mandated, many automotive manufacturers require it from their suppliers to ensure data security. Achieving compliance can be essential for maintaining business relationships and securing contracts.
Failure to comply with regulations can result in the loss of business opportunities, damage to your reputation, and increased vulnerability to cyber threats. It’s essential to prioritize compliance to protect your organization and its stakeholders.
Yes, NovaMDR specializes in helping SMEs navigate the complexities of becoming compliant. Our tailored solutions are designed to meet the unique needs and resources of smaller organizations.
However, please bear in mind that compliance has also other requirements for compliance besides the cybersecurity aspect, such as legal compliance, physical security, supplier management, awareness and training.
Getting started is easy! Contact us for a free consultation, and our team will assess your current security posture, discuss your needs, and develop a customized plan to help you achieve compliance efficiently.
Please wait while you are redirected to the right page...
When you visit our website, ForeNova and third parties can place cookies on your computer. These cookies are used to improve your website experience and provide more personalized services to you, both on this website and through other media. To find out more about the cookies we use, see our Privacy Policy.
If you reject all cookies, except one strictly necessary cookie, we won't track your information when you visit our site. In order to comply with your preferences, we'll have to use just one tiny cookie so that you're not asked to make this choice again.