BlackLock Ransomware Deep Dive: A Cross-Platform, Double Extortion Threat
Malicious File Summary
| Malware Family | BlackLock |
| Release Date | February 25, 2025 |
| Threat Type | Ransomware |
| Brief Description | BlackLock ransomware (also known as El Dorado or Eldorado) emerged in March 2024 and operates under a Ransomware-as-a-Service (RaaS) model. It employs a double extortion strategy—encrypting data and stealing sensitive information—and targets Windows, VMware ESXi, and Linux environments. Victims span various industries and regions. |
Sample Analysis
Summary
The sample requires administrator privilege to execute and must be run via the command line; it does not launch via double-click.
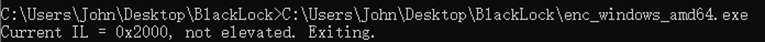
Upon execution, the following log is printed:
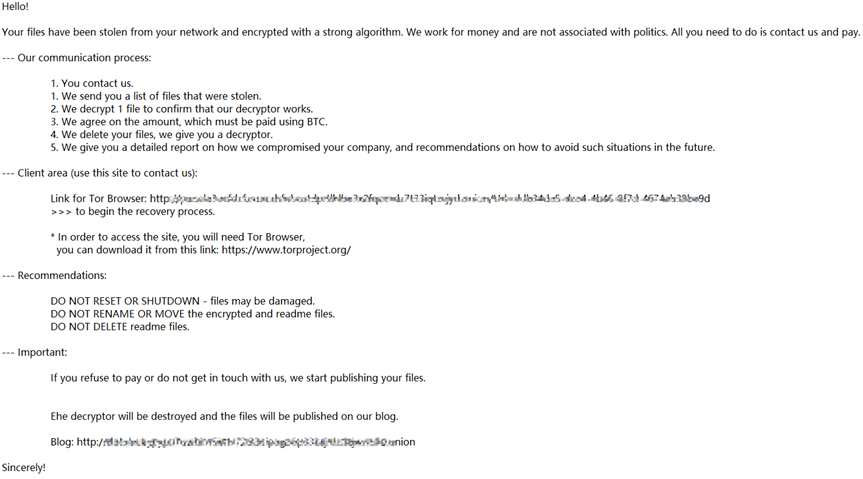
Ransom note content:HOW_RETURN_YOUR_DATA.TXT
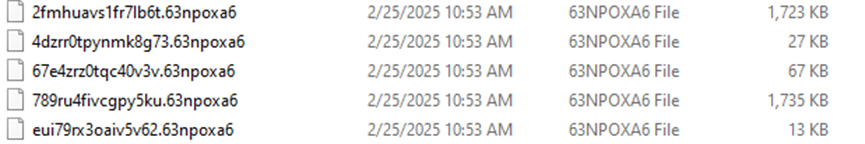
Example of encrypted files:
Analysis
Windows Version
Supported optional parameters for execution:
| Parameter | Description |
| -path | Specifies the file path to be encrypted |
| -skip-local | Specifies files to be excluded from encryption |
| -n <subnet> | Specifies shared resources in CIDR format, e.g., 192.168.5.0/24 |
| -d <domain> | Specifies the domain |
| -u <username> | Specifies SMB account |
| -p <password> | Specifies SMB password |
| -skip-net | Skips encrypting shared directories |
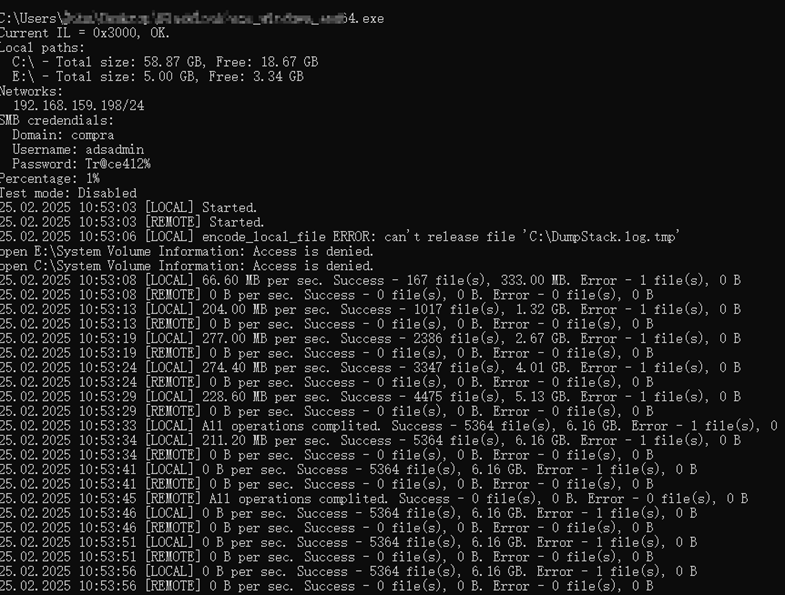
When provided with appropriate user credentials, it can encrypt files on shared networks using the SMB protocol.
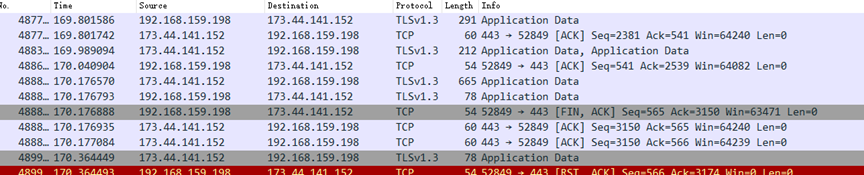
Logs are transmitted via WebSockets to 173.44.141[.]152, with the Origin header set to “http://logger”
To eliminate traces, the Eldorado ransomware runs a PowerShell command to overwrite the encryptor executables with random bytes and then deletes the file. If the “-keep” parameter is specified, this action is skipped:
$f=;
while(Test-Path -Path $f)
{
$o=new-object byte[] 10485760;
(new-object Random).NextBytes($o);
[IO.File]::WriteAllBytes($f,$o);
Remove-Item -Path $f;
Sleep 1;
}
Linux Version
The Linux variant is simpler, supporting only the -path parameter.
It recursively encrypts files within the specified directory using the same encryption algorithm as the Windows version.
Indicators of Compromise (IOC)
| SHA256 windows | 1375e5d7f672bfd43ff7c3e4a145a96b75b66d8040a5c5f98838f6eb0ab9f27b |
| 7f21d5c966f4fd1a042dad5051dfd9d4e7dfed58ca7b78596012f3f122ae66dd | |
| cb0b9e509a0f16eb864277cd76c4dcaa5016a356dd62c04dff8f8d96736174a7 | |
| 0622aed252556af50b834ae16392555e51d67b3a4c67a6836b98534a0d14d07d | |
| 8badf1274da7c2bd1416e2ff8c384348fc42e7d1600bf826c9ad695fb5192c74 | |
| SHA256 Linux | b2266ee3c678091874efc3877e1800a500d47582e9d35225c44ad379f12c70de |
| dc4092a476c29b855a9e5d7211f7272f04f7b4fca22c8ce4c5e4a01f22258c33 | |
| Malicious IP | 173.44.141.152 |
| Ransom Note Filename | HOW_RETURN_YOUR_DATA.TXT |
| Encrypted File Extensions | .63npoxa6、.00000001 |
| Dark Web URLs | http://dataleakypypu7uwblm5kttv726l3iripago6p336xjnbstkjwrlnlid.onion |
| Dark Web URLs | http://panela3eefdzfzxzxcshfnbustdprtlhlbe3x2fqomdz7t33iqtzvjyd.onion/Url=ddb34da5-dce4-4b46-8f7d-4674ab38be9d |
| Commandline | vssadmin delete shadows /all /quiet |
| Directories Excluded from Encryption | Windows, programdata, program files, program files (x86), $recycle.bin, all users, winnt, appdata, application data, local settings, boot |
| Files Excluded from Encryption | ntldr, ntdetect.com, autoexec.bat, ntuser.dat, ntuser.dat.log, iconcache.db, bootsect.bak, bootfont.bin, bootmgr, thumbs.db |
| File Extensions Excluded from Encryption | .00000001, .exe, .dll, .sys, .msi, .ini, .inf, .lnk,.63npoxa6 |






