A Deep Dive into Advanced Persistent Threats (APT)
You may well have heard of advanced persistent threats (APT) from recent high-profile APT attacks, such as the SolarWinds supply chain attack. But what are advanced persistent threats? How are they different from other cyber-attacks?
What is an APT Attack?
An advanced persistent threat (APT) is a cyber-attack in which the adversary operates undetected inside a compromised network for an extended period of time after gaining unauthorized access.
APT attacks are distinguished by their use of highly sophisticated tools and techniques to evade detection, steal credentials, and move through the network to reach high-value assets. These tools and techniques require significant financial and human capital to acquire or develop, implying that APT attacks are designed to target the meanest network defenses protecting important organizations and their assets. These organizations are typically government entities, critical infrastructure, and major enterprises. The goal is to steal sensitive data such as state secrets and intellectual property, conduct long-term cyber espionage, or disrupt social stability and endanger national security. The characteristics of an APT attack mean that only nation-states and state-sponsored organizations possess the resources and intent to carry out APT attacks. Indeed, most APT attacks have been attributed to various governments worldwide.
APT Attack Trends that Deserve Attention
While APT attacks have traditionally targeted high-value entities, several important trends have emerged in recent years that suggest smaller organizations or non-conventional APT targets are no longer safe from APT attacks.
Supply Chain Attacks
Advancements in cybersecurity technologies have increased the difficulty and costs of carrying out an APT attack. As a result, nation-state and state-sponsored APT threat actors are beginning to target non-conventional APT targets such as smaller enterprises with access to the real target’s network. By compromising a smaller entity with weaker defenses, APT attackers gain a more efficient way of breaching their ultimate target. This is significant as it means that smaller organizations that were unlikely targets are no longer immune from an APT attack.
Ransomware Attacks
Non-state-sponsored threat actors increasingly employ APT-style tactics, techniques, and procedures (TTPs) to feed their growing appetite for financial gain and mass disruption. Ransomware gangs, in particular, have leveraged these tools and techniques to not only encrypt more data, but also steal it. This form of double-extortion allows attackers to demand a larger ransom from their victims. The ever-increasing ransom figures demanded in ransomware attacks reflect this worrying trend.
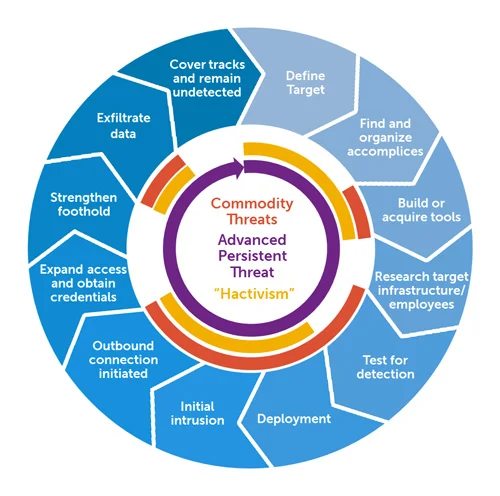
APT Attack Stages
An APT attack involves multiple stages that attackers must go through in order to achieve their objectives. The following section will describe the typical stages of an APT attack.
Image source: Wikipedia
Stage 1: Target Selection and External Reconnaissance
An APT attack always begins with identifying targets that satisfy the attacker’s objectives. Once a target has been selected, the attackers will perform a reconnaissance of the target to discover potential points of entry (attack vectors) and gather as much information on the target as possible.
Stage 2: Initial Access
After thorough preparation, the attacker attempts to gain unauthorized access to the target’s network by exploiting one or more viable attack vectors. One of the most common ways this is achieved is through highly deceptive social engineering techniques like spear-phishing emails. These emails are skillfully crafted to appear authentic and lure recipients into clicking a URL that downloads a malicious file. APT groups are also highly skilled at exploiting known and unknown 0-day vulnerabilities in system tools, services, software, and hardware to gain initial access. Intrusion through a supply chain attack is also gaining traction in light of recent high-profile attacks.
Stage 3: Malware Execution
After gaining access to the victim’s network, the attacker executes the first malware payload on the compromised machine (patient zero). This initial malware payload is used to achieve a variety of broader goals such as internal reconnaissance, defense evasion, and command and control communication.
- Internal Reconnaissance: The attacker leverage custom-loaded tools or legitimate system tools to scout the environment to figure out the location of high-value assets and plan the path of attack.
- Defense Evasion: The attacker uses tools and techniques to avoid detection. This includes uninstalling/disabling security software or leveraging trusted processes to hide and masquerade their malware.
- Command and Control: The attacker establishes command and control (C&C) communication between the compromised system and its infrastructure. C&C allows the attacker to remotely orchestrate the attack and can be used to open a backdoor for convenient network access and exfiltrate data.
Stage 4: Privilege Escalation and Lateral Movement
Once the attacker establishes a firm foothold on the compromised system, they begin to harvest access credentials (user, domain admin, and service accounts) to escalate their privileges. Escalated privileges give the attacker greater freedom and cover to operate and move laterally through the network to reach high-value targets that meet their objectives. Several native remote access services and remote control tools such as SMB, RDP, Windows Admin Shares, and PsExec enable attackers to access other systems in the network and perform actions like transferring malicious files, executing programs, and scheduling tasks.
Stage 5: Data Exfiltration and Damage Infliction
After reaching the high-value assets, the APT attacker begins exfiltrating the data from the target’s network to their own infrastructure. The data is typically transferred to a central location and packaged into an archive. The archive is encrypted to conceal it from deep packet inspection during exfiltration and compressed and chunked so that the data is exfiltrated in small enough quantities to resemble normal traffic activity, lowering any suspicion. The attacker may also create a smokescreen using a DDoS attack to draw the defender’s attention away from the exfiltration. Once data has been successfully exfiltrated, the APT attacker may decide to sabotage the victim’s environment depending on their objectives. For example, they may wipe the victim’s database, deface their website, or take over the infrastructure.
APT Attack Examples
The following section describes several prominent APT attacks that demonstrate different dimensions of an attack, including the type of target, the method of entry, the sophisticated techniques, and timeframe of attacks.
SolarWinds Supply Chain Attack
A list of prominent APT attacks is incomplete without mentioning the SolarWinds supply chain attack. “From a software engineering perspective, it’s probably fair to say that this is the largest and most sophisticated attack the world has ever seen,” said Microsoft President Brad Smith.
In December 2020, U.S. IT management software vendor SolarWinds was exposed as the victim of a major software supply chain attack. The attacker gained unauthorized access to the SolarWinds network as early as September 2019. The attackers compiled the Sunburst backdoor into the SolarWinds Orion Platform, a popular network monitoring software used by 33,000 customers. Orion customers started installing the trojanized software updates in March 2020, giving the attacker direct access to the networks of a reported 18,000 Orion customers. Victims were far-ranging, including the highest echelons of the U.S. government, including the Pentagon, Treasury, Homeland Security, and State Department. However, up to 80% of victims were large enterprises like Microsoft, Intel, and Cisco. The true scope of the attack remains unclear, but estimates put the total cost of the attack at $100B.
Marriot Hotels Data Breach (2018)
In late 2018, Marriot Hotels announced that they were victims of a large-scale data breach. The initial breach is reported to have occurred four years earlier in 2014. The attackers originally gained unauthorized access to the network of Starwood Hotels Group, which was acquired by Marriot two years later in 2016. The Starwood brand continued using Starwood’s legacy systems from before the acquisition, allowing the attackers to expand their access to the entire Marriot Group. On September 8, 2018, an internal security tool flagged a suspicious attempt to access Starwood’s internal guest reservation database. A user with administrator privileges made the database query, but analysis showed that the query was not made by the person to whom the account was assigned – an indication that someone else had hacked the account. The subsequent forensic investigation led to the revelation of the breach. Personal data of up to 339 million guests was breached, including extremely sensitive information such as passport and credit card numbers, making the attack one of the largest data breaches in history. Marriot Hotels was fined £18.4m due to data protection violations.
Ireland Health Service Executive Ransomware Attack
A destructive ransomware attack hit Ireland’s Health Service Executive (HSE) on May 14, 2021, with the attacker demanding a ransom of $20M. Ransomware attacks are not generally considered APT attacks due to their lack of sophistication and persistence within a network. However, the attack on HSE is an example of a ransomware threat actor employing APT-style TTPs in their attacks. The Conti ransomware gang gained access to HSE’s network on March 18, 2021, almost two months before the ransomware was executed. The breach resulted from an internal user clicking and opening a malicious Microsoft Excel file attached to a phishing email. Conti continued to operate in the HSE’s environment over an eight-week period. This included compromising a significant number of high privilege accounts and servers, exfiltrating data, and moving laterally to statutory and voluntary hospitals. Conti executed the ransomware on May 14, 2021, encrypting 80% of HSE’s systems. This led to severe disruptions of healthcare services throughout Ireland and leaked the information of thousands of Irish people after approximately 700 GB of data (including protected health information) was stolen from HSE’s network.
Stuxnet Worm Attack on Iranian Nuclear Facilities
Stuxnet is a computer worm discovered in June 2010 after an investigation was launched into the substantial damage suffered by the centrifuges at the Natanz nuclear enrichment laboratory in Iran. The Stuxnet worm is believed to have been introduced into Iran in June 2009, specifically targeting Iran’s nuclear enrichment facilities. The worm gained access to systems via a USB drive and spread to other Microsoft Windows PCs on the network. The worm scans the computer in search of the Siemens Step7 software that controls a programmable logic controller (PLC). If the Siemens software was not found, the worm laid dormant and was programmed to erase itself on a specific date. If the software is detected, Stuxnet downloaded a newer version of itself and exploited four 0-day vulnerabilities to ultimately inject malicious code into the software and PLC. This allowed the attacker to sabotage the enrichment centrifuges by controlling their speed to burn them out. The worm also manipulated the feedback from the centrifuges so that operators would not have been aware of the sabotage. The Stuxnet worm reportedly infected more than 200,000 machines in 14 Iranian facilities and may have ruined up to 10% of the 9,000 centrifuges in Natanz.
APT Detection and Protection Using NDR
It is clear that APT attacks are extremely stealthy and sophisticated. The successful compromise of major enterprises and top government organizations may leave us questioning whether detecting and defending against APT attacks is even possible.
Indeed, many cybersecurity solutions such as firewalls, endpoint security, intrusion detection and prevention systems may no longer offer adequate protection against APT attacks. Essentially, these tools are designed to prevent and detect known threats using known malware signatures, known indicators of compromise (IoC), and known attack patterns. With APT threat actors constantly updating their tools, TTPs, and infrastructure, what is really needed is a solution to detect non-signatured-based malware and unknown attack activity and patterns.
The answer is Network Detection and Response.
What is Network Detection and Response (NDR)?
Network detection and response (NDR) is a security solution that performs real-time monitoring and analysis of network-wide traffic to detect and respond to malware and behavioral-based malicious activity in the network.
Why NDR is Effective Against APT Attacks
The crux of NDR is detecting behavioral-based malicious activity. As stealthy as they are, APT activities generate network traffic in all stages of an attack, and as long as activities generate traffic, they can be detected. NDR leverages the power of machine learning, artificial intelligence, and behavioral analytics to analyze network traffic and detect granular deviations from normal network activity to uncover APT threats.
Detecting threats at the network layer is also effective because APT attackers rely on the network to carry out their activities, and therefore, it would be counterproductive for them to sabotage it. Moreover, NDR solutions have built-in decryption capabilities to see through any encrypted traffic attackers use to conceal their malicious actions and the exfiltration of data.
How NDR Detects and Responds to APT Threats
Detection: NDR continuously collects and normalizes raw network traffic in real time and extracts traffic metadata to a central location for machine analytics. A fundamental technology that underpins NDR is machine learning (ML). To detect malicious network activity, ML builds and dynamically optimizes baseline models of normal network activity for users, files, applications, endpoints, devices, and servers across the environment. Models for adversary tactics, techniques, and procedures are also incorporated to detect known attack patterns and behavior.
Metadata pulled from network traffic is analyzed with AI-powered behavioral and statistical analytics to identify anomalous activity. Behavioral analytics cross-references historical and real-time data to correlate seemingly unsuspicious events. Through behavioral analytics, NDR identifies signals showing user actions that break from patterns, like location or naming conventions, and looks at activity, apps, and accessed files to identify threats.
Response: NDR can not only detect potential threats but can provide complete visibility of threat history, that is, the timeline of malicious activity covering the whole cyber kill chain. In this case, security teams can answer a broad range of questions when responding to an incident. For example, they can answer: What did the asset or account do before the alert? What did it do after the alert? When did the situation start to escalate? In this way, NDR greatly empowers security teams with the knowledge for fast response and remediation.
NDR can be integrated with other cyber security solutions to initiate automated responses through SOAR (Security Orchestration, Automation, and Response). For example, once preconfigured SOAR playbooks are triggered, NDR can communicate with the network firewall to block IP addresses that are deemed malicious or instruct EDR to block and kill certain services, processes, and ports that show signs of malicious activity.