FBI Raids HIVE Ransomware Network
On January 26, 2023, the U.S. Department of Justice (DOJ) announced that the FBI had successfully taken down the network infrastructure of the notorious Hive Ransomware group.
Considered a top-five ransomware threat by the FBI, Hive Ransomware is responsible for over 1,500 attacks on victims in more than 80 countries, extorting over $100 million since June 2021.
According to the announcement, the coordinated operation with German law enforcement and Europol, among others, “seized control of the servers and websites that Hive uses to communicate with its members, disrupting Hive’s ability to attack and extort victims.” One of Hive’s websites on the dark web displayed the message, “The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against Hive Ransomware.”
Source: U.S. Department of Justice
The crackdown on Hive Ransomware comes after a months-long covert operation that saw the FBI infiltrate Hive computer networks in July 2022. Since gaining access to Hive’s networks, the FBI has provided over 300 decryption keys to new victims of Hive Ransomware attacks worldwide. “Using lawful means, we hacked the hackers. We turned the tables on Hive, and we busted their business model, saving potential victims approximately $130 million in ransomware payments,” said U.S. Deputy Attorney General Lisa O. Monaco in the press conference. U.S. Attorney General Merrick Garland revealed in his statement that victims that received decryption keys include a hospital in Louisiana asked to pay $3 million, a Texas school district blackmailed for $5 million, and a food services company facing a $10 million ransom demand.
A point of note came from FBI Director Christopher Wray, who revealed that only about 20% of identified Hive victims reached out to the FBI for help, a worrying indicator of the large number of ransomware attacks that get unreported and are left unknown.
However, statements by authorities did not reveal further information about the people behind the Hive Ransomware Group. “We will continue our investigation and pursue the actors behind Hive until they are brought to justice,” said Assistant Attorney General Kenneth A. Polite, Jr. of the Justice Department’s Criminal Division.
What is Hive Ransomware?
Hive is a prolific ransomware group, previously considered a top-five ransomware threat by the FBI, which claims that the group has been responsible for over 1,500 attacks on victims in more than 80 countries. According to the Justice Department, Hive has extorted over $100 million from its victims since the group was first observed in June 2021. Among the most targeted organizations by Hive include hospitals, school districts, financial institutions, and critical infrastructure.
Hive Ransomware operates using the Ransomware-as-a-Service (RaaS) model, where Hive operators develop and sell their ransomware to affiliates to launch attacks. In this model, Hive operators receive a 20% cut of the ransom payouts earned by Hive affiliates. Hive also practices double-extortion ransomware, where attackers first steal sensitive data from their victims before encryption. This is used to gain extra leverage over victims and pressure them to pay the ransom. Victims that refuse to pay will have their data published on Hive’s dark web leak site HiveLeaks.
A joint Cybersecurity Advisory released by the Cybersecurity and Infrastructure Security Agency (CISA) on November 17, 2022, warned that Hive affiliates gain initial access to victim networks through several methods. These include single-factor logins via Remote Desktop Protocol (RDP), virtual private networks (VPNs), and other remote network connection protocols; exploiting FortiToken vulnerabilities; sending phishing emails with malicious attachments; and exploiting Microsoft Exchange server vulnerabilities.
Microsoft’s Threat Intelligence Center (MSTIC) also warned in a July 5, 2022 publication that Hive had developed a new ransomware variant by switching its code from Go to the Rust programming language. Ransomware families written in Rust, such as BlackCat Ransomware, are gaining increasing notoriety due to their ability to work on multiple platforms and evade security detection.
Examples of Known Hive Ransomware Attacks
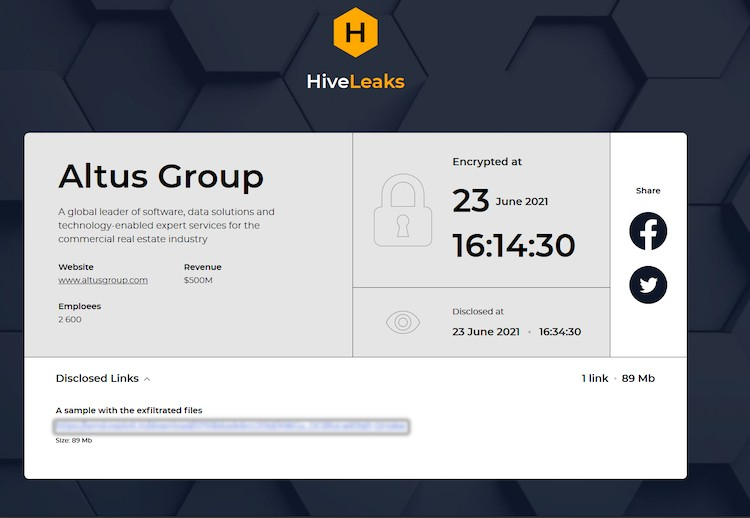
Altus Group: On June 14, 2021, Canadian commercial real estate software solutions firm Altus Group announced that it had experienced a cybersecurity incident. According to Cybernews, stolen data with a sample of exfiltrated files claimed to belong to Altus Group was the first to appear on Hive’s leak site, possibly making it one of Hive’s first victims.
Source: Cybernews
Memorial Health System: This US-based not-for-profit integrated health system fell victim to a Hive Ransomware attack on August 15, 2021, making it one of the group’s first healthcare victims. The attack disrupted clinical and financial operations, causing urgent surgeries and radiology exams to be canceled. At the same time, the sensitive data of over 200,000 patients was stolen, including social security numbers, names, and dates of birth.
MediaMarkt: On November 7, 2021, Europe’s largest consumer electronics retailer MediaMarkt suffered a Hive Ransomware attack that initially demanded an astronomical $240 million ransom. The attack paralyzed IT systems across the organization. Staff were asked not to use store computers and disconnect cash registers, meaning customers could not pay by card or obtain receipts.
Get Protected Against Ransomware with ForeNova
ForeNova offers a diverse range of enterprise cybersecurity products and services to help organizations prevent, detect, and respond to ransomware and all forms of cyber-attacks.
- NovaCommand: Gain complete visibility of and automate responses to threats missed by other security controls and hiding in your network.
- NovaIR: Call on our experienced cybersecurity incident response team to help you contain, investigate, and remediate cyber-attacks and recover and harden your systems.
- NovaMDR: Leverage a subscription-based service providing cutting-edge cybersecurity technologies and cybersecurity experts to monitor your networks 24/7.