Linux Ransomware: A Major Threat To Critical Infrastructure
RansomEXX (Defrat777)
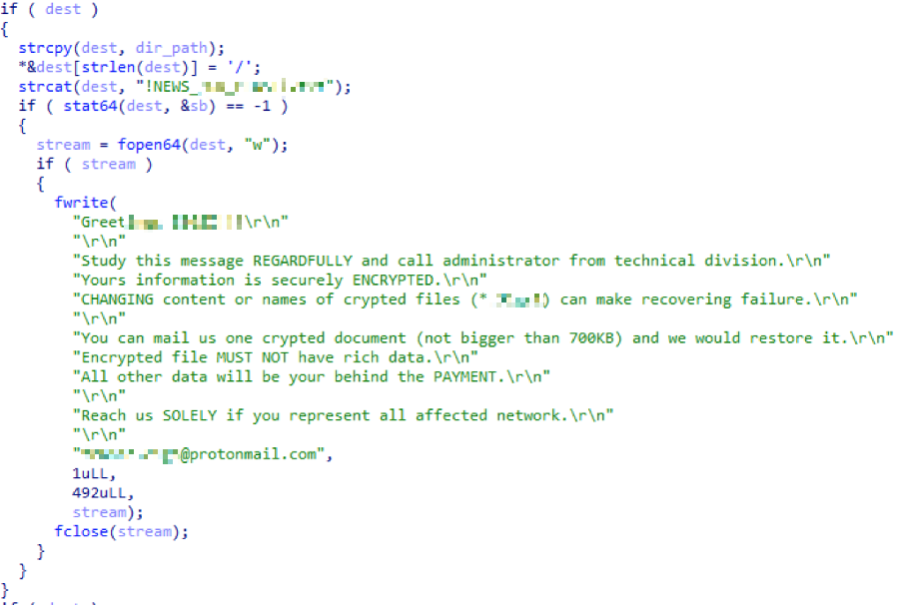
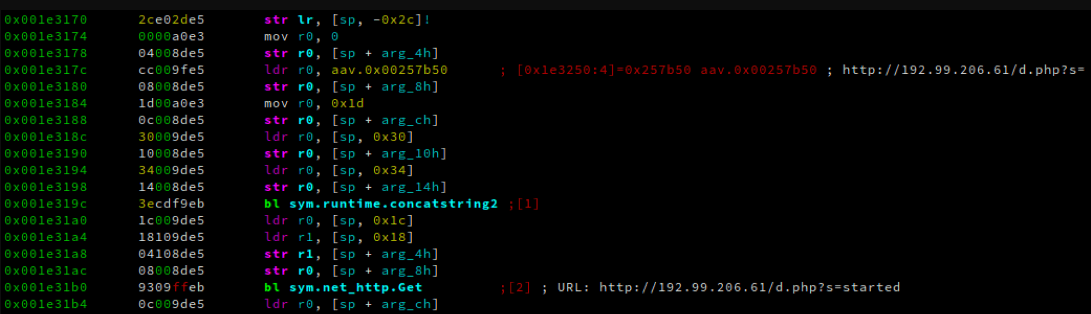
RansomEXX is a C-based 64-bit ELF binary, known for its targeted attacks against high-profile entities. Notable attacks occurred in 2020 and 2021, affecting organizations like the Brazilian government network and the Texas Department of Transportation. It requires human operation, with actors compromising networks and stealing credentials before spreading across devices. RansomEXX uses a 256-bit key for encrypting files and re-encrypts the AES key every second.
Image source: VMware blog
Attack Pattern
- RansomEXX is human-operated, requiring time for attackers to compromise a network, steal credentials, and spread across devices.
- It uses a 256-bit AES encryption key, which is further encrypted by a public RSA-4096 key. Notably, the ransomware re-encrypts the AES key every second.
- Targets have included high-profile organizations, indicating a preference for lucrative or high-impact targets.
Actionable Solutions
-
- Regularly update and patch systems to close vulnerabilities.
- Implement strict access controls and use multi-factor authentication.
- Conduct regular security training for staff to recognize phishing or social engineering attacks.
- Employ network segmentation to limit the spread of ransomware if a system is compromised.
Tycoon Ransomware
Tycoon is a Java-based ransomware that emerged in late 2019, targeting higher education organizations, software companies, and small to midsize businesses. It uses a booby-trapped ZIP archive with a malicious Java Runtime Environment component and typically breaches systems via unsecured remote desktop protocol ports. It uses AES and RSA-1024 for encryption and usually provides a 60-hour window for Bitcoin ransom payment. Source: https://phoenixnap.com/blog/linux-ransomware
Attack Pattern
- Tycoon infiltrates systems via an unsecured remote desktop protocol (RDP) port.
- It uses a booby-trapped ZIP archive with a malicious Java Runtime Environment component.
- The ransomware scrambles each file with a different AES key, then adds an RSA-1024 layer.
Actionable Solutions
- Secure and monitor RDP ports, and use VPNs for remote access.
- Implement antivirus and anti-malware solutions that can detect malicious Java components.
- Regular backups and disaster recovery plans are crucial for data restoration in case of an attack.
- Educate staff about the dangers of opening suspicious email attachments
Erebus Ransomware
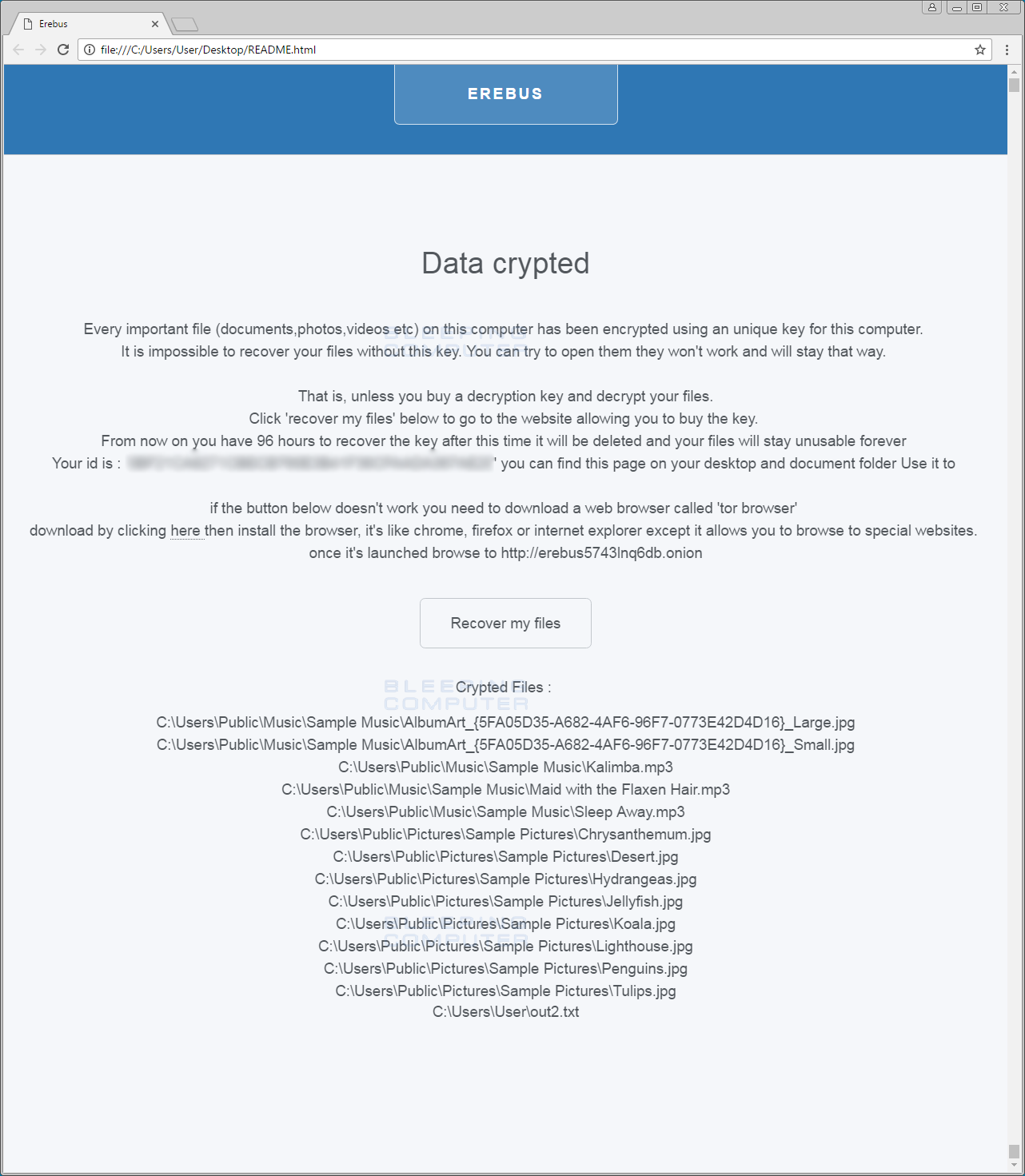
Initially targeting Windows, Erebus was repurposed for Linux servers, becoming notorious after a 2017 attack on a South Korean web hosting company. It affected over 3,400 client websites, leading to a significant ransom payment. Erebus scans for over 400 file types, including databases and documents, for encryption using RSA-2048, AES, and RC4 cryptosystems.
Image source: https://www.bleepingcomputer.com/
Attack Pattern
- Erebus scans a network for over 400 types of files, including databases, archives, and documents.
- Utilizes a combination of RSA-2048, AES, and RC4 cryptosystems for encryption.
- Known for high-profile attacks, like the one on a South Korean web hosting company.
Actionable Solutions
- Regularly update and backup all critical files and databases.
- Employ intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor and block suspicious activities.
- Segregate networks and use firewalls to limit lateral movement within the network.
- Train employees to recognize phishing and spear-phishing attempts
QNAPCrypt Ransomware
Appearing in July 2019, QNAPCrypt targets network-attached storage (NAS) Linux devices. It spreads through spam email campaigns, unofficial software activation tools, and fake software updates. This ransomware relies on flawed authentication practices and reaches out to a C2 server for an RSA public key to start file encryption.
Image source: https://www.anomali.com/blog/the-ech0raix-ransomware
Attack Pattern
- Targets network-attached storage (NAS) Linux devices.
- Spreads via spam email campaigns, unofficial software activation tools, and fake software updates.
- Exploits flawed authentication practices and uses a C2 server for key retrieval.
Actionable Solutions
- Implement strong authentication mechanisms and regularly change default credentials.
- Educate users about the risks of downloading and using unofficial software or clicking on email links/attachments from unknown sources.
- Keep NAS devices updated and monitor them for unusual activities.
- Use email filtering and anti-spam solutions to reduce the risk of phishing attacks
KillDisk Ransomware
Originally a Windows-only threat, KillDisk extended to Linux environments in January 2017. It overwrites the GRUB bootloader, preventing the target system from booting, and then displays a full-screen ransom note demanding Bitcoin payment. Due to its nature, data recovery might be impossible even after paying the ransom.
Image source: https://www.bleepingcomputer.com/
Attack Pattern
- Overwrites the GRUB bootloader, preventing systems from booting.
- Displays a full-screen ransom note demanding Bitcoin payment.
- There is skepticism about the feasibility of data recovery, even after ransom payment.
Actionable Solutions
- Implement strict controls over bootloaders and system startup configurations.
- Regularly backup systems, especially boot-related files.
- Conduct routine security audits to detect any unauthorized changes to system configurations.
- Employ advanced threat detection tools that can identify and block unusual bootloader modifications.
Other notable ransomware families in the Linux world include Mirai, Conti, DarkSide, REvil, and Hive. Mirai is a Linux-based trojan that infiltrates systems via Telnet and Secure Shell (SSH) to deliver brute-force attacks.
These kinds of ransomware draw attention to the growing complexity and diversity of attacks against Linux systems, highlighting the necessity of strong security protocols and knowledge of possible weaknesses in the Linux environment.
A common theme in actionable solutions includes maintaining up-to-date security patches, conducting regular backups, implementing strong access controls, and fostering a culture of cybersecurity awareness within the organization.
Additionally, employing comprehensive cybersecurity solutions, such as those offered by ForeNova, including 24/7 monitoring, real-time detection and response, and integration with existing security infrastructures, can significantly enhance an organization’s resilience against such sophisticated threats.