Noodlophile InfoStealer Unmasked: How AI Ads on Facebook Delivered a Python-Based Data Theft Chain
Attackers used Facebook to promote AI generated ads to lure users to a malicious website. The ad claimed to convert still images into vivid videos. After the fake progress bar reached 100%, users got a downloadable ZIP archive, which containd the following:
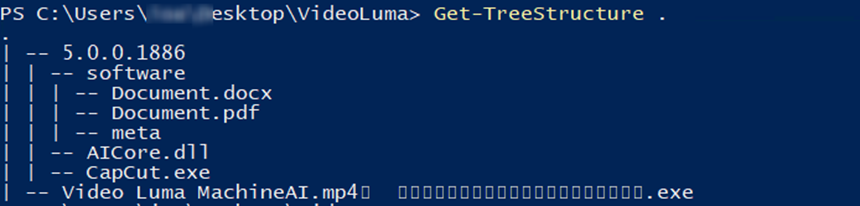
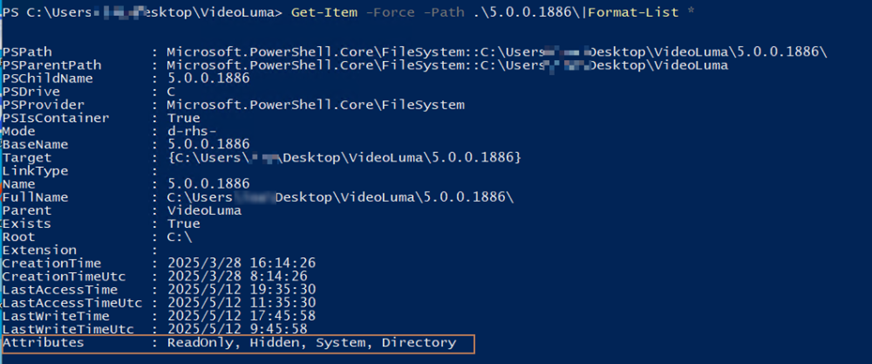
Among the contents was an executable file deceptively named “Video Luma MachineAI.mp4.exe”, multiple Unicode no-break space characters (\xe2\xa0\x80) were used between .mp4 and .exe to impersonate a video file. The folder 5.0.0.1886 had both system and hidden attributes, making it invisible by default in file explorers.
When the user double-clicks the .exe file, it runs “Capcut.exe” located in the 5.0.0.1886 directory and then exits the current process.

“CapCut.exe” is a .NET executable. Upon running, it repeatedly accesses “https[:]//google.com”, then briefly pauses. It then proceeds to rename files in the 5.0.0.1886\software directory, meta becomes “image.exe” and Document.docx becomes install.bat. The renamed image.exe is actually WinRAR, and install.bat is then executed.

The batch script decodes Document.pdf into ppIuqewlq.rar, which is silently extracted using “image.exe” into %LOCALAPPDATA%\SoftwareHost, with the extraction password being TONGDUCKIEMDEVELOPER2025. The extracted content includes a Python runtime environment and its dependencies. The file srchost.exe is essentially “python.exe”:

Using srchost.exe, the malware downloads and executes remote code. The downloaded script uses exec() to execute a marshaled (serialized) Python object. The marshaled object is then decompiled for analysis:
The disassembled opcodes amount to over 60,000 lines, but most are garbage instructions designed to hinder analysis. The meaningful opcodes are in the last 500 lines. To facilitate analysis, AI tools are used to reconstruct the original Python code from these opcodes.
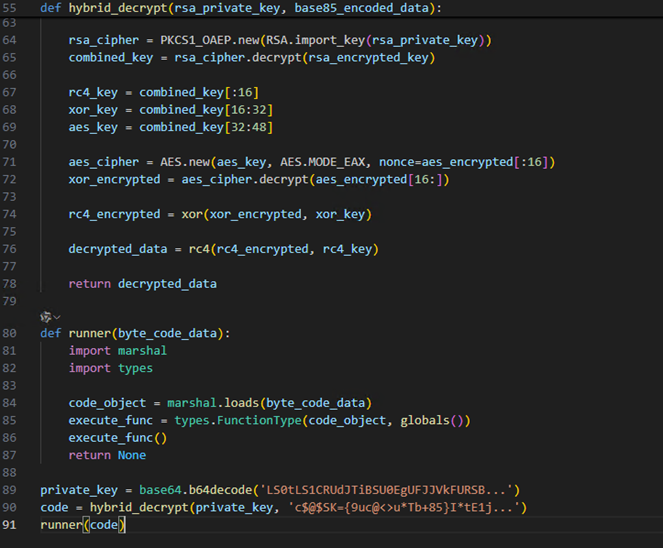
Although the AI-reconstructed code might differ from the original, it provides a helpful base for manual verification. Eventually, another marshaled object is uncovered, and the same decompilation method is applied to retrieve its source code.
The final code carries out data theft, targeting: Browser cookies, Browse history and saved credentials, Stored credit card information, Facebook login credentials and account data:


All stolen data is archived and sent to a Telegram bot before being deleted from the victim machine.






