What is Incident Response in Cyber Security
What is Incident Response in Cyber Security?
Incident response (also known as cyber incident response), refers to the process by which organizations respond to cyber security incidents like cyber-attacks and data breaches. Effective incident response can help organizations detect and contain cyber security threats in a timely manner so that losses and business disruptions are avoided or kept at a minimum.
How does Incident Response Work?
In standard practice, the incident response process should follow a formal incident response plan (IRP). The incident response plan should define an organization’s incident response efforts, including the personnel, technologies, and procedures that are involved. Different organizations will have their own unique process, but they typically follow the industry practices laid out by the SANS Institute or NIST (more details below).
Who is Responsible for Incident Response?
Incident response in large organizations is typically carried out by the in-house information security team. Small and midsize businesses (SMBs) that do not have full incident response capabilities (personnel and technologies) typically leverage the incident response services of cyber security companies, such as ForeNova’s NovaIR.
What is a Security Incident?
A security incident is a security event or a series of security events that actually or potentially threaten the confidentiality, integrity, and availability of an information system and the data the system processes, stores, or transmits. Security incidents include:
- Targeted cyber-attacks such as data breaches, ransomware attacks, spear-phishing attacks, supply chain attacks, DDoS attacks, advanced persistent threats (APT), and web attacks.
- Untargeted malware infections from phishing attacks, worm infections, drive-by downloads, and adware that lead to system failure, credential theft, botnet infection, crypto mining, etc.
- Insider threats from malicious or negligent employees that lead to data theft, data leaks, credential theft, and the introduction of malware and cyber-attacks into the network.
Security Incident vs. Security Event
Security events are observable occurrences in the network that can be harmless or malicious. If a security event is confirmed to cause actual or potential harm, the event is considered a security incident.

The Incident Response Process
There are two widely accepted industry standards for incident response, one from the SANS Institute and one from the National Institute of Standards and Technology (NIST). The SANS Institute incident response process is divided into six phases: preparation, identification, containment, eradication, recovery, and lessons learned. The NIST version condenses what is essentially the same process into four phases: preparation, detection and analysis, containment eradication and recovery, and post-incident activity. For this article, we will summarize the six phases of the SANS Institute’s incident response process.
The 6 Phases of Incident Response
- Preparation: The preparation phase involves activities that ensure the actual incident response is carried out efficiently and effectively. This is the phase where the incident response plan (IRP) is drawn up. The IRP should include, for example, the members of the computer security incident response team (CSIRT), each individual’s role, and whom to contact when an incident occurs. The required technologies should also be made available to ensure that incident responders have the necessary tools to conduct their work. Employees should also be trained on how to recognize suspicious events as their machines are most likely the ones that get compromised. Incident response drills should also be run regularly to test the effectiveness of the organization’s incident response plan and optimize it if
- Identification: The identification phase is where malicious and suspicious security events are detected, investigated, and confirmed as security incidents. The identification phase is mainly overseen by security tools that continuously work to detect known threats and suspicious behavior. Security operators subsequently investigate security device alerts and various log files to determine whether a security incident exists. Security teams may periodically scour through system logs, application logs, security device logs, and error messages to actively hunt for threats that were missed by security tools. Suspicious events may also be reported by employees and investigated by security operators to determine whether they are a threat.
- Containment: The containment phase is where the immediate threat is addressed to prevent or limit the short-term impact. Security tools often perform containment in real time, such as blocking a download from a suspicious IP address or quarantining known malware. Containment may also be manual, especially for threats that were missed by security tools and only identified after human For example, incident responders may take affected systems offline or isolate them so that the threat cannot spread to other systems. In fact, a certain amount of system downtime can be expected in the containment phase. However, for mission-critical systems that cannot afford downtime, incident responders may have to leave systems running and contain the threat through other means.
- Eradication: As alluded to above, containment is the short-term response to security incidents. However, residual threats may still exist in the environment, such as malware artifacts, backdoors, and auto-start entries. The eradication phase is where these residual threats are removed to prevent future compromise. Incident responders conduct a forensic investigation to discover the root cause of the security incident and how the attack progressed. They sift through various logs to reconstruct the complete attack path and remove any identified threats. In certain cases, complete systems are reimaged or restored from a clean backup.
- Recovery: The recovery phase is where affected systems are hardened and restored to production after the incident response team is confident that all threats have been eradicated from the environment. Systems hardening typically includes reconfiguring systems to address errors and weaknesses and installing patches to remediate vulnerabilities. Restored systems must be closely monitored for a period of time to ensure that they are no longer vulnerable. Ideally, the restored systems should be tested to ensure they can withstand the way they were previously exploited or by any other means.
- Lessons Learned: Lessons learned is a critical phase in the incident response process. It reviews the entire incident response process, from preparation to recovery, and concludes whether anything could have been done better. For example, in terms of preparation, did the incident response team follow the incident response plan? In terms of identification, how long did it take to identify and confirm the security incident? Do threat detection systems need to be optimized or upgraded? A well-executed lessons learned phase will enable the incident response team to respond more efficiently and effectively to future incidents in the long term.
Incident Response Tools
Various tools can be used in incident response. For this article, we advocate one particular tool – network detection and response – and explain why it is highly effective in various phases of the incident response process and, therefore, the choice of NovaIR.
What is Network Detection and Response?
Network detection and response (NDR) is a cyber security solution that is designed to detect advanced, unknown, and non-signature-based threats that have already breached a network.
In short, NDR solutions use machine learning to learn and build baselines of normal network behavior. It continuously applies AI and behavioral analytics to analyze and correlate traffic from across the network to compare real-time activity with baselines to detect anomalies. Any anomalous activity that indicates a threat is automatically responded to or flagged for further investigation.
If you’re interested in learning more about NDR, visit our NDR product page and watch a demo video to see how NDR works. The following article also provides a good explanation of NDR.
The Value of NDR in Incident Response
NDR in Threat Detection (Identification): NDR is an invaluable tool in the identification phase. On the one hand, NDR has superior threat detection capabilities. By focusing on detecting anomalous behavior as opposed to signatures, NDR is equipped to detect threats missed by traditional security tools, such as unknown and file-less malware. By correlating security events from multiple data sources, NDR makes better sense of individual events that appear innocuous to point solutions, thereby uncovering a chain of malicious activities that indicate a cyber-attack. In this sense, NDR is a holistic threat detection system that plugs the gaps between other security tools. Additionally, NDR can identify all devices connected to the network through continuous traffic monitoring. This is critical as it ensures that security incidents affecting all the organization’s assets are identified.
NDR in Threat Response (Containment): NDR solutions are integrated with other security tools, such as firewall and endpoint security software, to respond to identified threats. The beauty of NDR is that it can be configured to respond automatically to threats in what is known as security orchestration, automation, and response (SOAR). Security administrators can create incident response playbooks to define how NDR and other security tools respond to specific security incidents according to the organization’s needs. This ensures that threats are contained in real time once they are identified. The Cost of a Data Breach 2022 report found that organizations that deployed AI and automation were able to contain a breach 28 days faster than those that did not, saving an average of $3.05M.
NDR in Threat Hunting (Eradication): By correlating events across the network, NDR builds an integrated evidence chain of the attack, including the root cause and how it spread in the network. This intelligence allows security analysts to concentrate their threat-hunting efforts in specific areas instead of shifting through potentially thousands of logs. NDR essentially streamlines the threat-hunting process to ensure that residual threats are found and removed promptly.
NDR in Remediation (Recovery): The integrated evidence chain provided by NDR also reveals the vulnerabilities and errors that enabled the initial security breach and the subsequent propagation through the network to occur. Security teams can then apply the required patches and make changes to configurations to prevent future compromise. In fact, NDR does not only detect vulnerabilities during incident response but also during normal operations. With good patch management, security teams can use the vulnerability information provided by NDR to patch vulnerabilities before incidents occur.
The Importance of Incident Response
Cyber-attacks are inflicting increasingly more significant financial losses on organizations. The Cost of a Data Breach 2022 report found that the global average total cost of a data breach is $4.35M. More significantly, the report also observes that organizations that have an incident response team and regularly test their incident response plan saved $2.66M on average.
Apart from financial losses, organizations that suffer from the loss of confidential data may find themselves in trouble with regulators and face heavy penalties for compliance violations. Even customers may sue the organization for failing to protect their personal data. However, organizations that provide evidence of a well-thought-out incident response plan and detailed records of the incident response process can prove their due diligence and potentially avoid or reduce its liability.
How ForeNova NovaIR can Help
At ForeNova, we understand the immense pressure of being under a cyber-attack. More so when you don’t have the right processes and people in place to help figure out what is going on and what to do next.
Enter NovaIR, ForeNova’s incident response service, designed to help our customers resolve and investigate all kinds of security incidents with speed and precision. Our incident response team is backed by over 5,000 man-hours of incident response investigation experience and fine-tuned methodologies to haul victims out of their cyber-security nightmare.
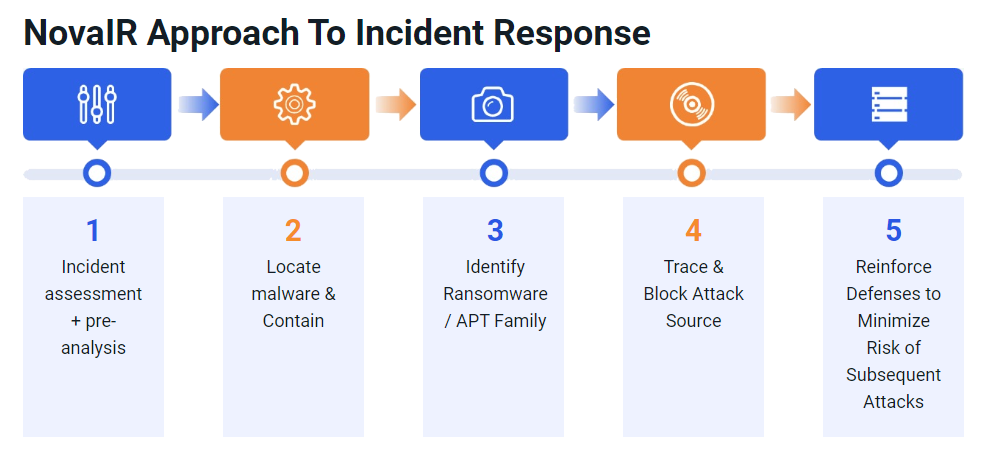
NovaIR Approach to Incident Response
The immediate focus of our NovaIR service is to assist customers in identifying and containing the attack. We then identify the root cause or point of entry and any vulnerabilities or weaknesses associated with the attack to eradicate any remaining threats in your environment. Finally, we provide a report that covers not only incident-related information, but also recommendations on how to further improve your security architecture based on industry best practices and the results of our investigation.