Summary
HellCat ransomware first appeared in 2024. It primarily spreads through spear-phishing email attachments and by exploiting vulnerabilities in applications such as Atlassian Jira and Palo Alto PAN-OS (e.g., CVE-2024-0012 and CVE-2024-9474). HellCat operates under a Ransomware-as-a-Service (RaaS) model, focusing on high-value targets and government entities. It provides affiliated actors with ransomware tools and infrastructure in exchange for a share of the profits.
Analysis
After execution, the ransomware displays a ransom note named “README.txt”. Victims are instructed to contact the attackers via an onion link or email. The note also includes an account and password.
Payload Details
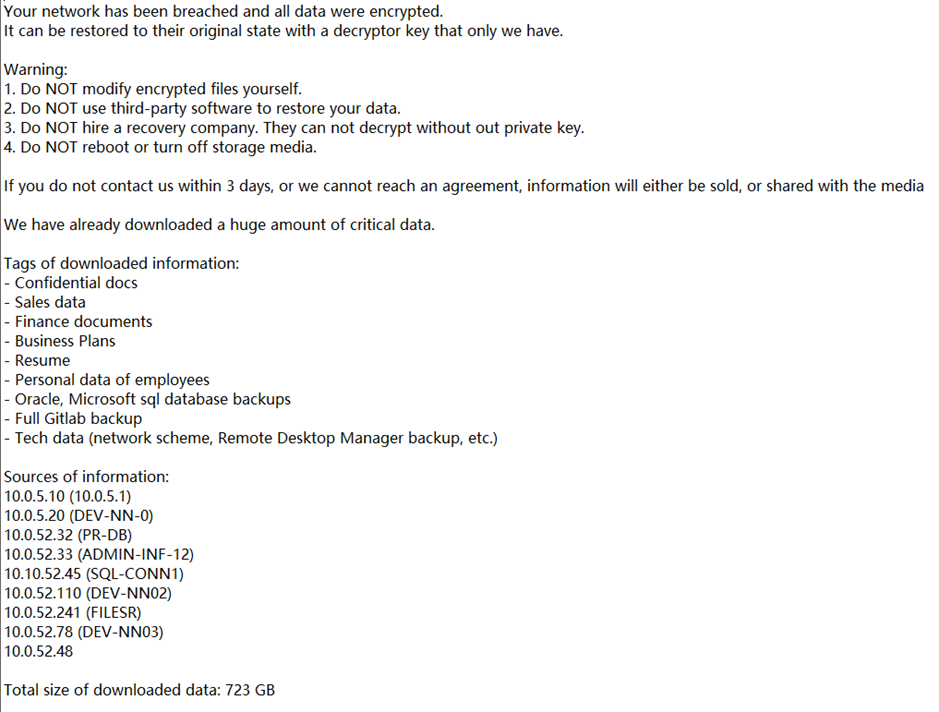
The HellCat payload is a standard 64-bit PE file, approximately 18KB in size, capable of encrypting specific directories or the full disk.
Encryption Method
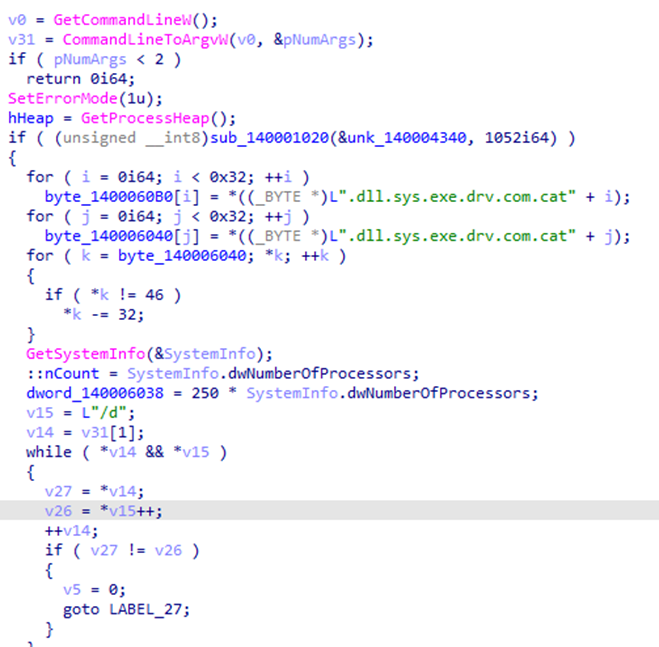
HellCat uses AES in CBC mode to encrypt files and secures the AES key with RSA encryption.
Self-Deletion Mechanism
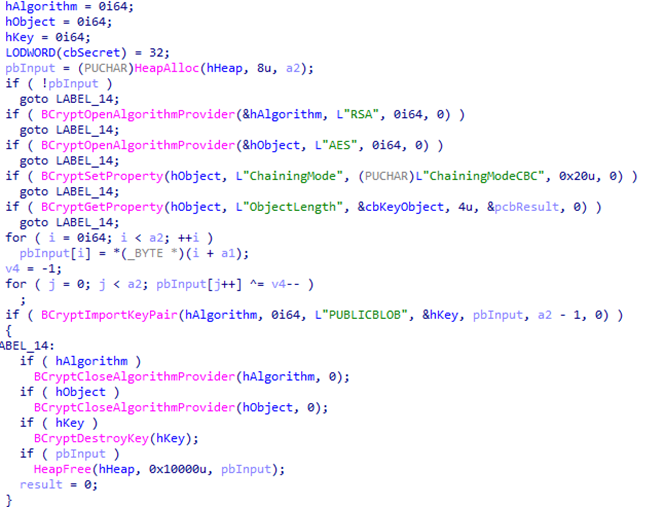
Additionally, HellCat utilizes Windows commands for self-deletion. If the ransomware sample is still present, it repeatedly tries to delete itself. This command is written to a file and executed, and it opens the ransom note file “_README_.txt” during this process.
Indicators of Compromise (IOC)
| SHA256 Hashes of HellCat Samples | 93aa8b0f950a7ea7f0cee2ba106efaacf673bb2b504ca0b9e87f9ea41acfb599 |
| 5b492a70c2bbded7286528316d402c89ae5514162d2988b17d6434ead5c8c274 | |
| Onion Link | hellcakbszllztlyqbjzwcbdhfrodx55wq77kmftp4bhnhsnn5r3odad.onion |
| File Extensions Excluded from Encryption | .dll .sys .exe .drv .com .cat |
Recommendations
- Regular Patching
Frequently check and update all software and operating systems—especially critical applications like Atlassian Jira and Palo Alto PAN-OS—to patch known vulnerabilities (e.g., CVE-2024-0012 and CVE-2024-9474). - Principle of Least Privilege
Limit user access to systems and data based on their roles, ensuring that only authorized users can access sensitive information and critical systems. - Security Monitoring and Response
Implement security event monitoring and incident response mechanisms to detect and respond to potential threats in a timely manner, minimizing the impact of attacks.


